الكشف عن التجسس الأمريكي واسع النطاق 2013
 مراقبة وكالة الأمن القومي |
|---|
 |
الكشف عن التجسس الأمريكي واسع النطاق 2013 mass surveillance disclosures، يشير إلى عدد من التقارير الإعلامية بدأت في يونيو 2013 والتي كشفت عن تفاصيل عملياتية لوكالة الأمن القومي الأمريكية وشركائها الدوليين في التجسس واسع النطاق على المواطنين الأجانب وكذلك المواطنين الأمريكيين. سلسلة التقارير كانت ضمن مخزون وثائق بالغة السرية سربها المقاول السابق لوكالة الأمن القومي إدوارد سنودن. في 6 يونيو 2013، نشرت أول مجموعة من الوثائق مجمعة على صفحات واشنطن پوست وگارديان، لافتة انتباه الجماهير. حسب گلن گرينوالد، الصحفي في گارديان، فهذه الوثائق كشفت عن "نطاق التجسس المحلي في عهد اوباما".[1]
ممارسة التجسس واسع النطاق في الولايات المتحدة تم في الأربعينيات واتسع نطاقه في السبعينيات. وسرعان ما تطور إلى برنامج تجسس عالمي اسمه الرمزي "إتشلون"،[2] لكنه لم يلفت الكثير من انتباه العامة حتى ظهرت برامج التجسس العالمية الأخرى مثل پريزم، إكس-كيسكور، وتمپورا ضمن آلاف الوثائق التي تم تسريبها في 2013.[3] الكثير من البلدان حول العالم، وتشمل الحلفاء الغربيين وعدد من دول الناتو، كانت مستهدفة من التحالف الاستراتيجي "فايڤ أيز" لأستراليا، كندا، نيوزيلندا، والمملكة المتحدة، والديمقراطيات الغربية الخمسة المتحدثة بالإنگليزية، المملكة المتحدة والولايات المتحدة بهدف تحقيق توعية معلوماتية كاملة عن طريق mastering the Internet وأدوات تحليل مثل Boundless Informant.[4] كما أكد مدير وكالة الأمن القومي كايث ب. ألكسندر في 26 سبتمبر 2013، قامت وكالة الأمن القومي بجمع وتخزين جميع السجلات الهاتفية لجميع المواطنين الأمريكيين.[5] معظم هذه المعلومات محفوظة في مرافق تخزين كبيرة مثل مركز بيانات يوتاه، مشروع عملاق قيمته 1.5 بليون دولار تم الإشارة إليه في وال سترير جرنال "كرمز لبراعة وكالات التجسس."[6]
نتيجة لتلك التسريبات، قامت حركات اجتماعية مثل رستور ذه فورث بالتظاهر احتجاجاً على التجسس واسع النطاق. برامج التجسس المحلية في بلدان مثل فرنسا، المملكة المتحدة، الهند تم شراؤها أيضاً لنفس الهدف. على الجانب القضائي، انضمت مؤسسة الحدود الإلكترونية في ائتلاف من جماعات مختلفة ورفعت دعوى قضائية على وكالة الأمن القومي. دعت مختلف منظمات حقوق الإنسان ادارة اوباما بعدم الملاحقة، لكن بحماية "سنودن المنبه للفساد". تضمنت الجماعات منظمة العفو الدولية، هيومان رايتس واتش، الشفافية الدولية ومؤشر الرقابة.[7][8][9][10]
في 14 يونيو 2013، أدين سنودن من قبل المدعين الفدراليين بمقتضى قانون التجسس 1917 لسرقته أملاك حكومية. بعدها حصل على لجوء سياسي مؤقت من الحكومة الروسية في أواخر يوليو 2013. ساهم هذا في توتر العلاقات الأمريكية الروسية.[11][12] في 6 أغسطس 2013، ظهر الرئيس الأمريكي اوباما على شاشة التلفزيون الوطني حيث طمأن الأمريكيين بأنه "ليس لدينا برامج تجسس محلية" و"لا يوجد تجسس على الأمريكيين".[13]
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
خلفية تاريخية

ظهر الكشف عن برنامج التجسس واسع النطاق على المواطنين الأمريكيين في الإعلام الأمريكي في 2006.[15] في أوائل 2013، سلم إدوارد سنودن أكثر من 15.000 - 20.000 وثيقة بالغة السرية إلى وسائل الإعلام المختلفة، مثيراً واحدة من أكبر التسريبات الإخبارية في التاريخ الأمريكي المعاصر.[16]
أصول التجسس السري في الولايات المتحدة

أثناء الحرب العالمية الثانية دخلت الحكومة البريطانية والأمريكية في سلسلة من الاتفاقيات للمشاركة في تجسس إشارات على حركة اتصالات العدو.[19] في مارس 1946، تم التوقيع على اتفاقية سرية، "الاتفاقية الأمريكيةالبريطانية للتجسس على الاتصالات"، والمعروفة باسم بورسا، بمقتضى اتفاقيات الحرب. الاتفاقية "ربطت بلدين بشبكة عالمية بمراكز تصنت يديرها مركز الاتصالات الحكومية، أكبر منظمة تجسس في المملكةالمتحدة، ونظيره الأمريكي، وكالة الأمن القومي."[20]
الرقابة وقت الحرب على الاتصالات أثناء الحروب العالمية كانت متزامنة مع فك رموز الاتصالات وقت السلم بواسطة الحجرة السوداء (مكتب الشفير، إم أي-8)، الذي كان يدار بموافقة من وزارة الخارجية الأمريكية من 1919 حتى 1929.[21] عام 1945 تأسس مشروع شامروك السابق لجمع البيانات التلغرافية الواردة والصادرة من الولايات المتحدة.[21][22] شركات الاتصالات الكبرى مثل وسترن يونيون، أر سي إيه العالمية وأي تي تي للاتصالات ساعدت بنشاط الحكومة الأمريكية في محاولتها التالية للدخول على حركة الرسائل الدولية.[23]
مكتب التحقيقات الفدرالي تحت رئاسة ج. إدگار هوڤر قام بعملية تجسس واسعة النطاق على الاتصالات والخطاب السياسي، مستهدفاً الكثير من المتحدثين المعروفين مثل ألبرت أينشتاين،[14][24][25] فرانك سيناترا،[26][27] السيدة الأولى إلينور روزڤلت،[28][29] مارلين مونرو،[30] جون لينون،[31] مارتن لوثر كينگ، الإبن،[32][33] في مذكرة صادرة من مكتب التحقيقات الفدرالي تشير إلى كينگ على أنه "الزعيم الزنجي الأكثر خطراً وتأثيراً في البلاد"،[34] دانيال إلسبرگ،[35][36] كشف النقاب عن هذه الأنشطة فيما بعد أثناء التحقيقات فيما عرف باسم فضيحة وترگيت والتي تكشفت ببطئ، والتي أدت في النهاية إلى استقالة الرئيس ريتشارد نيكسون.[37]
عام 1952، تأسس مكتب الأمن القومي رسمياً.[21] حسب نيويورك تايمز، تأسس مكتب الأمن القومي في "سرية مطلقة" بواسطة الرئيس ترومان.[38] بعد ستة أسابيع من تولي الرئيس ترومان السلطة، أمر بالتصنت على هواتف توماس گاردينر كوركوران، المستشار المقرب من فرانكلين روزڤلت.[39] المحادثات المسجلة محفوظة حالياً في المتحف والمكتبة الرئاسية لهاري س. ترومان، مع وثائق حساسة أخرى. (~233,600 pages)
التحريات: لم يسأل أحد: هل هي أخلاقية؟
It did not matter that much of the information had already been released —or leaked—to the public. The effect was still overwhelming: a stunning, dismaying indictment of U.S. intelligence agencies and six Presidents, from Franklin Roosevelt to Richard Nixon, for having blithely violated democratic ideals and individual rights while gathering information at home or conducting clandestine operations abroad...
التجسس واسع النطاق في السياق العالمي (1940–2001)


عام 1988، في مقالة نشرها دونكان كامبل في "نيو ستيتمان"، بعنوان "شخص ما يستمع"، وصف فيها مخابرات الشرات بأنها تجمع أنشطة برنامج اسمه الرمزي إتشلون.[45] كان البرنامج يدار من قبل حلفاء الحرب العالمية الثانية المتحدثون بالإنگليزية، أستراليا، كندا، نيوزيلاندا، المملكة المتحدة والولايات المتحدة (يعرفون جميعاً باسم AUSCANNZUKUS). بمقتضى اتفاقية اوكوسا، تأسس البرنامج لمراقبة الاتصالات العسكرية والدبلوماسية لحلفاء الاتحاد السوڤيتي والكتلة الشرقية أثناء الحرب الباردة في أوائل الستينيات.[46] على الرغم من وجوده لفترة طويلة، إلا أن اتفاقية اوكوسا أعلنت للعامة فقد عام 2010. تمكن الاتفاقية الولايات المتحدة والمملكة المتحدة من تبادل "المعلومات المجمعة من الاتصالات الأجنبية التي يتم اعتراضها، فك شفراتها وترجمتها". تنهي الاتفاقية معرفة أي طرف ثالث بوجودها.[20]
في أواخر التسعينيات، كان نظام إتشلون قادراً على اعتراض البث بالقمر الصناعي، اتصالات شبكة الهواتف العامة المحولة، البث عن طريق الموجات الصغرى. قدم صحفي نيوزيلاندي، نيكي هاگر وصف مفصل لإتشلون في كتابه المنشور عام 1996، "القوى السرية". في الوقت الذي نفت فيه الحكومات الأعضاء وجود إتشلون، إلا أن تقرير نشره الپرلمان الاوروپي عام 2011، أكد استخدام البرنامج وحذر الاوروپيون منه.[2] أعلن الپرلمان الاوروپي في تقريره أن مصطلح "إتشلون" كان يستخدم في عدة سياقات، لكن هناك أدلة تشير إلى أنه نظام جمع معلومات استخباراتي قادر على اعتراض ومراقبة مكالمات الهاتف، الفاكس، والبريد الإلكتروني وحركة بيانات أخرى عالمية. أكد التقرير أن هذا كان "نظام عالمي لاعتراض الاتصالات الخاصة والتجارية."[46]
الكشف عن شبكة تجسس إتشلون
تخيل أن شبكة تجسس عالمية يمكنها التصنت على كل اشارة مكالمة هاتفية، فاكس، أو بريد إلكتروني، في أي مكان على الكوكب. يبدو أن هذا نوع من الخيال العلمي، لكنه حقيقة. إثنان من المدافعين الرئيسيين - بريطانيا وأمريكا - أنكرا رسمياً وجوده. لكن بي بي سي حصلت على تأكيد من الحكومة الأسترالية أن هذه الشبكة موجودة بشكل حقيقي..."
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
9/11 وآثارها على التجسس واسع النطاقا (2001–2009)


في أعقاب هجمات 11 سبتبمر 2011 على مركز التجارة العالمي والپنتاگون، إزدات عمليات التجسس المحلية في الولايات المتحدة بشكل ملحوظ. في محاولة لمنع وقوع هجمات مستقبلية على هذا النطاق تم تمرير القانون الوطني. فيما بعد مررت قوانين منها قانون حماية أمريكا (والذي حذف شرط الحصول على مذكرة لمراقبة الحكومة الأهداف الأجنبية[51]) وقانون تعديلات فيسا (والذي يخفف من التقيد ببعض المتطلبات الأصلية في محكمة فيسا).
عام 2005، أعلن توماس تام عن وجود ستيلارويند. في 1 يناير 2006، بعد أيام من نشر نيويورك تايمز أن "بوش سمح للأمريكيين بالتجسس على المتصلين بدون محاكم"،[52] أكد الرئيس الأمريكي أن "هذا هو برنامج محدود تم تصميمه لمنع الهجمات على الولايات المتحدة الأمريكية. وأكرر، محدود."[53]
في 2006، أعلن [[مارك كلاين] عن وجود روم 641إيه، الذي يعود عمله إلى 2003.[54] عام 2008، باباك پاسدار، خبير في أمن الحاسوب، والرئيس التنفيذي لبات بلو أعلن للعامة عن وجود "دائرة كوانيتكو"، الذي اكتشفها هو وفريقه عام 2003. وصفها على أنها باب خلفي للحكومة الأمريكية داخل أنظمة موفر الخدمة اللاسلكية، لم يذكر اسمه؛ فيما بعد عرف أنه ڤريزون.[55]
أنت مشتبه به
كل عملية شراء تقوم بها بواسطة بطاقة ائتمان، كل اشتراك مجلة تقوم بها وكل وصفة طبية تقوم بملئها، كل موقع وب تزوره ورسالة إلكترونية ترسلها أو تستقبلها، كل درجة أكاديمية تحصل عليها، كل حساب مصرفي تملكه، كل رحلة تحجز لها، كل حدث تحضره - كل المعاملات والاتصالات التي تقوم بها تذهب إلى وزارة الدفاع في قاعدة بيانات مركزية كبرى. هذا الملف المحوسب لحياتك الخاصة من مصادر تجارية، يضيف كل معلومة عنك لدى الحكومة - بيانات جواز السفر، رخصة القيادة، وسجلات الرسوم، السجلات القضائية وسجلات الطلاق، شكاوى الجيران المزعجين إلى مكتب التحقيقات الفدرالي، ورقة عن حياتك بالإضافة إلى أحدث كاميرا تجسس مخفية -- حلم التجسس المزعج الذي يراودك: الوعي المعلوماتي الإجمالي عن كل مواطن أمريكي
— نيويورك تايمز، نوفمبر 2002[56]
تسارع التسريبات الإعلامية (2010–الآن)
On 28 November 2010, WikiLeaks and five major news outlets in Spain (El País), France (Le Monde), Germany (Der Spiegel), the United Kingdom (The Guardian), and the United States (The New York Times) began publishing the first 220 of 251,287 leaked U.S. State department diplomatic "cables" simultaneously.[57]
Other notable media leaks include the Afghan War documents leak (considered to be one of the largest leaks in U.S. military history[58]), as well as the Iraq War documents leak (A collection of 391,832 United States Army field reports[59]), and the Guantanamo Bay files leak (779 top secret documents marked NOFORN).
On 15 March 2012, the American magazine Wired published an article with the headline "The NSA Is Building the Country's Biggest Spy Center (Watch What You Say)",[60] which was later mentioned by U.S. Rep. Hank Johnson during a congressional hearing. In response to Johnson's inquiry, NSA director Keith B. Alexander testified that these allegations made by Wired magazine were untrue.[61]
الوكالة الأمريكية تنفي مراقبة مركز البيانات للبريد الإلكتروني للمواطنين
"Many unfounded allegations have been made about the planned activities of the Utah Data Center," the NSA said in a statement, noting that "one of the biggest misconceptions about NSA is that we are unlawfully listening in on, or reading emails of, U.S. citizens. This is simply not the case.".
ملخص تفاصيل التجسس المكشوفة






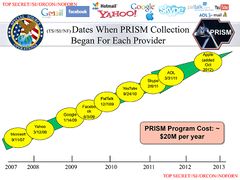
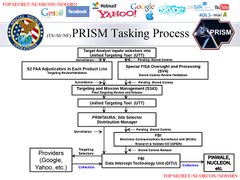
On 6 June 2013, Britain's The Guardian newspaper began publishing a series of revelations by an as yet unknown American whistleblower, revealed several days later to be ex-CIA and ex-NSA-contracted systems analyst Edward Snowden. Snowden gave a cache of documents to two journalists: Glenn Greenwald and Laura Poitras, Greenwald later estimated that the cache contains 15,000 – 20,000 documents, some very large and very detailed, and some very small.[70][71] In over two subsequent months of publications, it became clear that the NSA had operated a complex web of spying programs which allowed it to intercept internet and telephone conversations from over a billion users from dozens of countries around the world. Specific revelations were made about China, the European Union, Latin America, Iran and Pakistan, and Australia and New Zealand, however the published documentation reveals that many of the programs indiscriminately collected bulk information directly from central servers and internet backbones, which almost invariably carry and reroute information from distant countries.
Due to this central server and backbone monitoring, many of the programs overlapped and interrelated among one another. These programs were often carried out with the assistance of US entities such as the United States Department of Justice and the FBI,[72] were sanctioned by US laws such as the FISA Amendments Act, and the necessary court orders for them were signed by the secret Foreign Intelligence Surveillance Court. Some of the NSA's programs were directly aided by national and foreign intelligence agencies, Britain's GCHQ and Australia's DSD, as well as by large private telecommunications and internet corporations, such as Verizon, Telstra,[73] Google and Facebook.[74]
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
الأهداف
According to the April 2013 summary of documents leaked by Snowden, other than to combat terrorism, these surveillance programs were employed to assess the foreign policy and economic stability of other countries,[75] and to gather "commercial secrets".[76]
In a statement addressed to the National Congress of Brazil in early August 2013, journalist Glenn Greenwald maintained that the U.S. government had used counter-terrorism as a pretext for clandestine surveillance in order to compete with other countries in the "business, industrial and economic fields".[77][78][79]
In an interview with Der Spiegel published on 12 August 2013, former NSA Director Michael Hayden admitted that "We (the NSA) steal secrets. We're number one in it". Hayden also added: "We steal stuff to make you safe, not to make you rich".[75]
According to documents seen by the news agency Reuters, these "secrets" were subsequently funnelled to authorities across the nation to help them launch criminal investigations of Americans.[80] Federal agents are then instructed to "recreate" the investigative trail in order to "cover up" where the information originated.[80]
المستهدفون
According to the April 2013 summary of disclosures, the NSA defined its "intelligence priorities" on a scale of "1" (highest interest) to "5" (lowest interest).[75] It classified about 30 countries as "3rd parties", with whom it cooperates but also spies on:
- Main targets: China, Russia, Iran, Pakistan and Afghanistan were ranked highly on the NSA's list of spying priorities, followed by France, Germany, Japan, and Brazil. The European Union's "international trade" and "economic stability" are also of interest.[75] Other high priority targets include Cuba, Israel, and North Korea.[81]
- North Korea: Despite being a priority target, and despite continuous surveillance from sensors located outside the country, the NSA knew little about North Korea and Kim Jong Un.[81]
- Syria: Syria was being closely monitored, particularly for signs of chemical weapons use.[81]
- Iran: suspected nuclear sites that did not show up on satellite imagery were identified by new surveillance techniques.[81]
- Irrelevant : From a US intelligence perspective, countries such as Cambodia, Laos and Nepal were largely irrelevant, as were most European countries like Finland, Denmark, Croatia and the Czech Republic.[75]
Other prominent targets included members and adherents of the internet group known as "Anonymous",[75] as well as potential whistleblowers.[82] According to Edward Snowden, the NSA targeted reporters who wrote critically about the government after 9/11.[83]
As part of a joint operation with the Central Intelligence Agency (CIA), the NSA deployed secret eavesdropping posts in eighty U.S. embassies and consulates worldwide.[63] The headquarters of NATO were also used by NSA experts to spy on the European Union.[84]
In 2013, documents provided by Edward Snowden revealed that the following intergovernmental organizations, diplomatic missions, and government ministries have been subjected to surveillance by the "Five Eyes":
| البلد/ المنظمة |
الهدف | الوسائل |
|---|---|---|
| وزارة الطاقة | Collection of metadata records by the Communications Security Establishment of Canada (CSEC)[85] | |
| وزارة الشؤون الخارجية والاوروپية | Infiltration of virtual private networks (VPN)[86] | |
| سفارة فرنسا في واشنطن دي سي | ||
| سفارة الهند في واشنطن دي سي |
| |
| الممثل الدائم للهند في الأمم المتحدة | ||
| وزير الأمن العام | ||
| مجلس الاتحاد الاوروپي في بروكسل |
| |
| وفد الأمم المتحدة في نيويورك | ||
| وفد الولايات المتحدة في واشنطن دي سي | ||
| مقر الأمم المتحدة في نيويورك |
| |
| الوكالة الاوروپية للطاقة الذرية في ڤيينا |
التعاون الدولي

During الحرب العالمية الثانية, the BRUSA Agreement was signed by the governments of the United States and the United Kingdom for the purpose of intelligence sharing.[19] This was later formalized in the UKUSA Agreement of 1946 as a secret treaty. The full text of the agreement was released to the public on 25 June 2010.[20]
Although the treaty was later revised to include other countries such as Denmark, Germany, Ireland, Norway, Turkey, and the Philippines,[20] most of the information sharing has been performed by the so-called "Five Eyes",[91] a term referring to the following English-speaking western democracies and their respective intelligence agencies:
 – The Defence Signals Directorate of Australia[91]
– The Defence Signals Directorate of Australia[91] – The Communications Security Establishment of Canada[91]
– The Communications Security Establishment of Canada[91] – The Government Communications Security Bureau of New Zealand[91]
– The Government Communications Security Bureau of New Zealand[91] – The Government Communications Headquarters of the United Kingdom, which is widely considered to be a leader in traditional spying due to its influence on countries that were once colonies of the British Empire.[91]
– The Government Communications Headquarters of the United Kingdom, which is widely considered to be a leader in traditional spying due to its influence on countries that were once colonies of the British Empire.[91] – The National Security Agency of the United States, which has the biggest budget and the most advanced technical abilities among the "five eyes".[91]
– The National Security Agency of the United States, which has the biggest budget and the most advanced technical abilities among the "five eyes".[91]
In 2013, media disclosures revealed how other government agencies have cooperated extensively with the "Five Eyes":
 - The Politiets Efterretningstjeneste (PET) of Denmark, a domestic intelligence agency, exchanges data with the NSA on a regular basis, as part of a secret agreement with the United States.[92]
- The Politiets Efterretningstjeneste (PET) of Denmark, a domestic intelligence agency, exchanges data with the NSA on a regular basis, as part of a secret agreement with the United States.[92]
 – The Bundesnachrichtendienst (Federal Intelligence Service) of Germany systematically transfers metadata from German intelligence sources to the NSA. In December 2012 alone, Germany provided the NSA with 500 million metadata records.[93] The NSA granted the Bundesnachrichtendienst access to X-Keyscore,[94] in exchange for Mira4 and Veras.[93] In early 2013, Hans-Georg Maaßen, President of the German domestic security agency BfV, made several visits to the headquarters of the NSA. According to classified documents of the German government, Maaßen had agreed to transfer all data collected by the BfV via XKeyscore to the NSA.[95] In addition, the BfV has been working very closely with eight other U.S. government agencies, including the CIA.[96]
– The Bundesnachrichtendienst (Federal Intelligence Service) of Germany systematically transfers metadata from German intelligence sources to the NSA. In December 2012 alone, Germany provided the NSA with 500 million metadata records.[93] The NSA granted the Bundesnachrichtendienst access to X-Keyscore,[94] in exchange for Mira4 and Veras.[93] In early 2013, Hans-Georg Maaßen, President of the German domestic security agency BfV, made several visits to the headquarters of the NSA. According to classified documents of the German government, Maaßen had agreed to transfer all data collected by the BfV via XKeyscore to the NSA.[95] In addition, the BfV has been working very closely with eight other U.S. government agencies, including the CIA.[96]
 - The SIGINT National Unit of Israel routinely receives raw intelligence data (including those of U.S. citizens) from the NSA.[97] (See also: Memorandum of understanding between the NSA and Israel)
- The SIGINT National Unit of Israel routinely receives raw intelligence data (including those of U.S. citizens) from the NSA.[97] (See also: Memorandum of understanding between the NSA and Israel)
 - In 2011, the Japanese government was asked by the NSA to intercept fiber-optic cables carrying phone and Internet data from across the entire Asia-Pacific region, including China. However, the Japanese government refused to comply.[98]
- In 2011, the Japanese government was asked by the NSA to intercept fiber-optic cables carrying phone and Internet data from across the entire Asia-Pacific region, including China. However, the Japanese government refused to comply.[98]
 - The Algemene Inlichtingen en Veiligheidsdienst (General Intelligence and Security Service) of the Netherlands has been receiving and storing user information gathered by U.S. intelligence sources such as PRISM.[99]
- The Algemene Inlichtingen en Veiligheidsdienst (General Intelligence and Security Service) of the Netherlands has been receiving and storing user information gathered by U.S. intelligence sources such as PRISM.[99]
 – The Defence Ministry of Singapore and its Security and Intelligence Division have been secretly intercepting much of the fibre optic cable traffic passing through the Asian continent. Information gathered by the Government of Singapore is transferred to the Government of Australia as part of an intelligence sharing agreement. This allows the "Five Eyes" to maintain a "stranglehold on communications across the Eastern Hemisphere".[100]
– The Defence Ministry of Singapore and its Security and Intelligence Division have been secretly intercepting much of the fibre optic cable traffic passing through the Asian continent. Information gathered by the Government of Singapore is transferred to the Government of Australia as part of an intelligence sharing agreement. This allows the "Five Eyes" to maintain a "stranglehold on communications across the Eastern Hemisphere".[100]
 – The National Defence Radio Establishment of Sweden (codenamed Sardines)[101] has been working extensively with the NSA, and it has granted the "five eyes" access to underwater cables in the Baltic Sea.[101]
– The National Defence Radio Establishment of Sweden (codenamed Sardines)[101] has been working extensively with the NSA, and it has granted the "five eyes" access to underwater cables in the Baltic Sea.[101]
 - The Federal Intelligence Service (FSI) of Switzerland regularly exchanges information with the NSA, based on a secret agreement.[92][102] In addition, the NSA has been granted access to Swiss monitoring facilities in Leuk (canton of Valais) and Herrenschwanden (canton of Bern).[92]
- The Federal Intelligence Service (FSI) of Switzerland regularly exchanges information with the NSA, based on a secret agreement.[92][102] In addition, the NSA has been granted access to Swiss monitoring facilities in Leuk (canton of Valais) and Herrenschwanden (canton of Bern).[92]

Left: SEA-ME-WE 3, which runs across the Afro-Eurasian supercontinent from Japan to Northern Germany, is one of the most important submarine cables accessed by the "Five Eyes". Singapore, a former British colony in the Asia-Pacific region (blue dot), plays a vital role in intercepting internet and telecommunications traffic heading from Australia/Japan to Europe, and vice versa. An intelligence sharing agreement between Singapore and Australia allows the rest of the "Five Eyes" to gain access to SEA-ME-WE 3.[100]
Right:TAT-14, a telecommunications cable linking Europe with the United States, was identified as one of few assets of "Critical Infrastructure and Key Resources" of the USA on foreign territory. In 2013, it was revealed that British officials "pressured a handful of telecommunications and internet companies" to allow the British government to gain access to TAT-14.[103]
According to the leaked documents, aside from the Five Eyes, most other Western countries also participatied in the NSA surveillance system and sharing information with each other.[104] However, being a partner of the NSA did not automatically exempt a country from being targeted by the NSA. According to an internal NSA document leaked by Snowden, "We (the NSA) can, and often do, target the signals of most 3rd party foreign partners."[105]
الوسائل
التسريبات من الهواتف الذكية
As worldwide sales of smartphones began exceeding those of feature phones, the NSA decided to take advantage of the smartphone boom. This is particularly advantageous because the smartphone combines a myriad of data that would interest an intelligence agency, such as social contacts, user behavior, interests, location, photos and credit card numbers and passwords.[106]
An internal NSA report from 2010 stated that the spread of the smartphone has been occurring "extremely rapidly"—developments that "certainly complicate traditional target analysis."[106] According to the document, the NSA has set up task forces assigned to several smartphone manufacturers and operating systems, including Apple Inc.'s iPhone and iOS operating system, as well as Google's Android mobile operating system.[106] Similarly, Britain's GCHQ assigned a team to study and crack the BlackBerry.[106]
Under the heading "iPhone capability," the document notes that there are smaller NSA programs, known as "scripts," that can perform surveillance on 38 different features of the iPhone 3 and iPhone 4 operating systems. These include the mapping feature, voicemail and photos, as well as Google Earth, Facebook and Yahoo! Messenger.[106]
First slide: "Who knew in 1984..."(A reference to George Orwell's dystopian novel Nineteen Eighty-Four)
Second slide:"...that this would be big brother..." (Referring to Steve Jobs of Apple Inc. and the iPhone brand)
Third slide:"...and the Zombies would be paying customers?""السيطرة على الإنترنت"
"Mastering the Internet" (MTI) is part of the Interception Modernisation Programme (IMP) of the British government that involves the insertion of thousands of DPI (deep packet inspection) "black boxes" at various internet service providers, as revealed by the British media in 2009.[108]
In 2013, it was further revealed that the NSA had made a £17.2 million financial contribution to the project, which is capable of vacuuming signals from up to 200 fibre-optic cables at all physical points of entry into Great Britain.[109]
| السيطرة على الإنترنت |
|---|
|

طائرات الاستطلاع بدون طيار
On 19 June 2013, FBI Director Robert Mueller told the United States Senate Committee on the Judiciary that the federal government had been employing surveillance drones on U.S. soil in "particular incidents".[115] According to Mueller, the FBI is currently in the initial stage of developing drone policies.[115]
Earlier in 2012, Congress passed a US$63 billion bill that will grant four years of additional funding to the Federal Aviation Administration (FAA). Under the bill, the FAA is required to provide military and commercial drones with expanded access to U.S. airspace by October 2015.[116]
In February 2013, a spokesman for the Los Angeles Police Department explained that these drones would initially be deployed in large public gatherings, including major protests. Over time, tiny drones would be used to fly inside buildings to track down suspects and assist in investigations.[117] According to The Los Angeles Times, the main advantage of using drones is that they offer "unblinking eye-in-the-sky coverage". They can be modified to carry high-resolution video cameras, infrared sensors, license plate readers, listening devices, and be disguised as sea gulls or other birds to mask themselves.[117]
By 2020, about 30,000 unmanned drones are expected to be deployed in the United States for the purpose of surveillance and law enforcement.[118]
الكشف حسب التصنيف 2013
طلبات المحكمة، المذكرات ووثائق الشرطة
- Memorandum of understanding between the NSA and the Israel SIGINT National Unit (ISNU)
- April 2013 FISC Order demanding that Verizon hand over all telephony metadata to NSA. The order had been initially granted in May 2006. In 2009 the FISC discovered that the government had made repeated and substantial misrepresentations to the court about its use, and had routinely been "running queries of the metadata using querying terms that did not meet the required standard for querying." It further concluded that the violations had been routine and systematic.[119]
- Legal Justification of the bulk telephony metadata collection (officially released)[120]
- 2009 NSA Procedures for Targeting Foreigners for Surveillance
- 2009 NSA Procedures for Minimizing collection on US Persons
- 2011 NSA Procedures for Minimizing collection on US Persons (officially released)[121]
- Reference to a 2011 Change in the court-approved Minimization Procedures allowing analysts to run search queries using US persons' identifiers if there is "effective" oversight by NSA (it is not publicly known if such oversight has been established, or if any such searches have been conducted).[122] The court order mentioned was later officially released.[123]
- October 2011 Court decision finding NSA's upstream collection program, which collected tens of thousands of non-target communications, to have violated the law. It held, citing multiple Supreme Court precedents, that the Fourth Amendment applies to the contents of all communications, whatever the means (they are "papers"). It also finds that the NSA's minimization and targeting policies to be legally and/or constitutionally deficient, and recommends changes. (officially released).[123][124][125][126][127][128][129][130][131][132] Additional findings:
- The collection of Upstream data had begun before a court order approving it, in violation of 50 USC § 1809(a), which makes it a crime to engage in, use or disseminate surveillance knowing, or having reason to know such surveillance was not authorized. [133]
- March 2009 FISC ruling showing a consistent pattern of misrepresentations of the bulk telephone metadata collection program by the government to the Court. It also held that the data was being routinely queried in ways that did not meet "reasonable articulatable suspicion", demonstrating inadequate safeguards in the software and training of analysts. Showing that "thousands of violations resulted from the use of identifiers that were not "RAS-approved by analysts who were not even aware that they were accessing BR metadata," and that in 2006 "there was no single person [in the NSA] who had a complete understanding of the BR FISA system architecture," a situation which persisted until February 2009 or later. RAS is shorthand for Reasonable Articulatable Suspicion. The Court nonetheless reapproved the collection of bulk phone metadata, while mandating additional safeguards and training, and "end-to-end system engineering reviews," and reports from the review. (Officially released by court order)[134][135][136][137][138][139][140]
- October 2012 Presidential Policy Directive 20 (PPD20), outlining cyberwarfare.
- 2007 Michael Mukasey memo proposing broader powers.
- April 2013 list of US Spying targets and topics by priority. The top priority countries are: Iran, Russia, China, Pakistan, North Korea and Afghanistan. Germany, France, the European Union, and Japan are mid-level priorities; Italy and Spain rank lower.[141][142]
- FY 2013 Intelligence "Black Budget" Summary.[81][143]
- A memorandum of understanding concerning US sharing of raw SIGINT with Israel. The data has not been scrubbed to eliminate US persons, it asks Israel not to deliberately target US persons, however the agreement allows Israel to retain US person data for one full year. The memorandum is not legally binding. A separate document states "And there are other kinds of CI threats that are right on our midst. For example, one of NSA's biggest threats is actually from friendly intelligence services, like Israel.", it continues "Balancing the SIGINT exchange between US and Israeli needs has been a constant challenge. In the last decade, it arguably tilted heavily in favor of Israeli security concerns. 9/11 came and went, and with NSA's only true Third Party CT relationship being driven almost entirely driven by the needs of the partner." [144]
- September 13, 2013 FISC Court order declassifing all the legal opinions relating to Section 215 of the Patriot Act written after May 2011 that aren't already the subject of Freedom of Information Act litigation. The FISA Court ruled that the White House must identify the opinions in question by October 4, 2013.[145][146][147]
التقارير
- 2009 OIG report on STELLARWIND
- Extracts from reports relating to XKeyscore. One entitled "Tales from the Land of Brothers Grimm" and others detailing the successes of said software, another is a note from an analyst who felt that he always had one foot in prison when using it. XKeyscore is also described as "big and scary, strong and powerful" and lets an analyst do whatever they like.[148]
- Reports detailing thousands of privacy violations[149]
- Numerous reports relating to drones, including "Threats to Unmanned Aerial Vehicles", a report summarizing attempts to shoot down, intercept, control or otherwise spoof drones. While the report details vulnerabilities of specific aircraft, the document itself has not been published, but only excerpts described. Other reports detail American spin efforts, suggesting that the phrases "drone strike," "kill list," "robot warfare," "Aerial Assassins" be avoided, offering "lethal UAV operations" instead, and also terms like "Pre-emptive and Preventive Military Action" and "Inherent Right of Self Defense." Likewise, reports detail efforts by Al-Qaeda to spin, portraying attacks as cowardly and immoral. Analysts also questioned whether America was losing rhetorical battle in courts, media, and public opinion. Another report stated that drone strikes "could be brought under increased scrutiny, perceived to be illegitimate, openly resisted or undermined."[150]
- The US learned that Pakistan engaged in a pattern of extrajudicial killings, mostly against militants. However, not all targets militants, Pakistan also planned to murder a human rights activist, Asma Jahangir, while she was on a visit to India. The plot was aborted when she learned of it. The US sought to avoid public disclosure of this, and other incidents.[151][152]
- The NSA and GCHQ have access to user data in iPhones, Blackberries, and Android phones. They are able to read almost all smartphone information, including SMS, location, emails, and notes.[153]
Collection and analysis programs or hardware
- Boundless Informant – Computer program that physically performs the data collection.[154]
- Dropmire – A program that specifically targets foreign embassies and diplomats
- XKeyscore – A program which allows searching collected data in a variety of ways.[155][156]
- SHELLTRUMPET – A metadata program that targets international communications.[157]
- Unified Targeting Tool (UTT) – A graphical frontend for querying databases.[155][158]
- LOPERS – A software based system to spy on PSTNs[159]
- TURBULENCE – Includes cyber-warfare capabilities, such as targeting enemies with malware. (updates to existing knowledge)
- JUGGERNAUT – A system to intercept mobile networks, including voice, fax, data, and text.[159]
- SPYDER[155]
- CHALKFUN[155]
- VLR – Visitor Location Register[155]
- TransX[155]
- RAGTIME – A blanket term for any of four different surveillance programs[155][160]
- Special Collection Service – Joint CIA/NSA eavesdropping team focused based in about 80 US embassies and consulates around the world. There are known branches in Frankfurt and Vienna. According to Der Spiegel, many of their operations are a direct violation of at least 3 signed treaties: "The Convention on the Privileges and Immunities of the United Nations of 1946, the Vienna Convention on Diplomatic Relations of 1961, and a signed an agreement in 1947 that rules out all undercover operations.[161]
- STATEROOM – Surveillance on embassies and consulates. Highly Classified.[161]
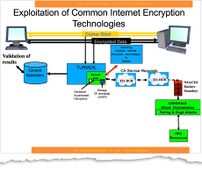
- BULLRUN, named after the Battle of Bull Run. - Bullrun refers to the NSA's set of codebreaking capabilities, including the use of Computer Network Exploitation (hacking) to obtain keys, weakening of encryption standards and providing backdoors to the same.[162] The following codenames are known to be related to BULLRUN: APERIODIC, AMBULANT, AUNTIE, PAINTEDEAGLE, PAWLEYS, PITCHFORD, PENDLETON, PICARESQUE, and PIEDMONT. No further explanation of the above codenames has been provided to date.[163]
- Edgehill, named after the Battle of Edgehill - A program similar to BULLRUN, operated by the GCHQ.[162]
العلاقة بالشركاء
- Special Source Operations (SSO) – Is a division of the NSA responsible for all programs which collaborate with corporate entities.[72]
- Upstream collects data from fiber-optic cables and internet backbones.[164][165]
- Codenames of companies participating in Upstream: BLARNEY (a surveillance program which was established by the NSA with AT&T and which operates at or near key fiber-optic landing points in the U.S. to capture foreign communications coming in and out of the country),[166][167] STORMBREW, FAIRVIEW (a highly classified program for tapping into the world's intercontinental fiber-optic cables according to NSA whistleblower Thomas Andrews Drake),[167] and OAKSTAR. There are conflicting sources: some that call these "programs",[166][168][169] versus the official statement called "The National Security Agency: Missions, Authorities, Oversight and Partnerships" that describes them as codenames of cooperating companies.[170][171] A third source, just released groups them with describes them as "programs authorized to collect cable transit traffic passing through US Gateways with both sides of the communication being foreign.[155]The FY 2013 budget for the above programs is as follows:[172]
- Miscellaneous codenames of companies: LITHIUM[170]
- RAMPART – Described as being part of Special Source operations, there is at least one known subdivision.[173]
- RAMPART-T – Started in 1991 or earlier, documents describe this program as: "Penetration of hard targets at or near leadership level". The information is intended for "the president and his national security advisers". Rampart-T is aimed at China, Russia, and Eastern European countries, there are around 20 nations targeted.[161]
- Microsoft allows the NSA to bypass encryption on Outlook.com.
- Names and Codenames of companies assisting GCHQ:
- Verizon Business (codenamed "Dacron")
- British Telecommunications (codenamed "Remedy")
- Vodafone Cable (codenamed "Gerontic")
- Global Crossing (codenamed "Pinnage")
- Level 3 (codenamed "Little")
- Viatel (codenamed "Vitreous")
- Interoute (codenamed "Streetcar")
قواعد بيانات وكالة الأمن القومي
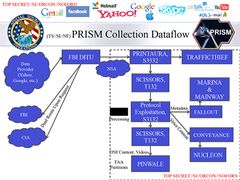
- PINWALE – Stores email and text[174]
- NUCLEON – Stores voice data[175]
- MAINWAY – Stores telephony metadata (ie call records)[176]
- MARINA – Stores Internet metadata[174][176]
- TRAFFICTHIEF – Stores metadata from a subset of assigned targets.
- CLOUD/ABR[155]
- DISHFIRE[155]
- FASTSCOPE[155]
- SIGINT NAVIGATOR[155]
- TRACFIN - A database of financial information.[155][177]
- TUNINGFORK[155]
- OCTAVE – A database with a graphical frontend[155][158]
- ANCHORY – A database of completed SIGINT reports.[155][175]
- Nymrod – Apparently a database of names (appears in UTT Screenshot)[158]
Signals intelligence directorates (SIDs)
- PRINTAURA – According to Ambinder, "NSA Unit involved in data filtering for TRAFFICTHIEF"[175]
- Protocol Exploitation – Sorts data types into specific databases[165][175]
الادارات التقنية
الأسماء المرتبطة بالأهداف المحددة
- Apalatchee = The EU mission by the East River, in New York.[161]
- Magothy = The EU embassy in Washington, DC. This embassy had its internal videoconferencing, and other areas of the computer network tapped. Both by the US, and by the Chinese. The US effort was conducted by the team working for the BLARNEY program.[161]
- Wabash = French diplomatic office in Washington. This office was bugged.[178]
- Blackfoot = French diplomatic office in the UN in New York. This office was bugged and computer screen captures obtained.[178]
- KATEEL = Brazilian embassy in Washington.[179]
- POCOMOKE = Brazilian Permanent Mission to the UN in New York.[179]
الأسماء الرمزية الغير مصنفة أو الغير موصفة بشكل كافي
- CERF CALL MOSES1[159]
- CONVEYANCE – Provide filtering for PRISM.[165]
- EVILOLIVE- Collects internet traffic and data.[157]
- FACELIFT[173]
- FALLOUT – Provides filtering for PRISM .[165]
- LONGHAUL - Involved in the process of decrypting communications.[162]
- MATRIX[159]
- MOONLIGHTPATH[157][180][181]
- SPINNERET[157][180][181]
- STEELKNIGHT[182]
- CASPORT[155]
- DANCINGOASIS[161]
عمليات الاتصالات الحكومية
The Government Communications Headquarters (GCHQ) is the main British intelligence agency responsible for providing signals intelligence (SIGINT) and information assurance to the British government and armed forces.
- Tempora – Collects data from transatlantic fibre-optic cables of major telecommunications corporations by directly tapping on them and from Internet backbones. Tempora uses intercepts on the fibre-optic cables that make up the backbone of the internet to gain access to swaths of internet users' personal data. The intercepts are placed in the United Kingdom and overseas, with the knowledge of companies owning either the cables or landing stations. It is a GCHQ program to create a large-scale "Internet buffer" which stores Internet content for three days and metadata for up to 30 days.[165][183][184]
- Britain runs a large-scale intercept station in the Middle East, capable of tapping underwater fiber-optic cables and satellites, and extracting email, telephone, and web traffic. The information is then passed to the GCHQ and shared with the NSA. The operation costs around £1 billion and is still being assembled. It is part of the "Tempora" project.[185] Edward Snowden disputes the Independent's claim that he, or anyone he has had direct contact with is the source of this information.[186] Süddeutsche Zeitung's fiber optic revelations were also described as having been obtained from GC-Wiki by Snowden.[103]
- GCHQ is believed to have forced some six global telecommunications and Internet companies to allow them to access more than 14 fiber optic cables that transport telephone communications.[103] The six companies, BT, Vodafone, Viatel, Interoute, Verizon and Level-3, gave GCHQ access to the cables in return for payment, it is believed the companies had no choice in this decision.[103] Three of the cables' terminal stations are on German territory; two of the cables are partially owned by Deutsche Telekom, who have denied knowledge of or participation in GCHQ's activities.[103]
- Spying on the 2009 G20 Summit in London.
- Life and times of GCHQ employees.
- GC-Wiki – An internal wiki at GCHQ.[185]
- Access to the majority of Internet and telephone communications throughout Europe, and occasionally as far as the United States.[103]
- GCHQ has a team dedicated to cracking encrypted traffic on Hotmail, Google, Yahoo and Facebook.[162]
- The Belgian telecom company Belgacom reports that it had been hacked, and has filed criminal charges, and will be cooperating with the investigation into the hacking. "The inquiry has shown that the hacking was only possible by an intruder with significant financial and logistic means," they said. "This fact, combined with the technical complexity of the hacking and the scale on which it occurred, points towards international state-sponsored cyber espionage." [187] According to documents released by Der Spiegel, the operation against Belgacom was entitled 'Operation Socialist' and was done by the GCHQ for the purpose of enabling Man-in-the-middle attacks against smartphones.[188][189]
عمليات وكالة الأمن القومي
- Hacking Tsinghua University, and also Pacnet in China.
- Spying on Latin America with the help of Global Crossing.
- The NSA operates "Special Collection Services," a global monitoring network, that collects from more then 80 embassies and consulates worldwide, often without the knowledge or consent of the host country.[90][190]
- The NSA spied on a UN videoconferencing system, in violation of the US agreement with the UN not to do so. In the process NSA discovered that the Chinese had already done so, and then started analyzing what the Chinese were taking. Shortly thereafter, the NSA gained access to approximately 500 other UN channels of communications.[90][190][191]
- Additional details of the raid on Osama bin Laden's Abbotabad, Pakistan compound. The work of Tailored Access Operations, in installing spyware on phones is highlighted. Also highlighted are the roles of the CIA, other agencies, and the Navy SEALs.[192]
- The NSA's Network Analysis Center cracked the reservation system for Aeroflot, and also hacked Al Jazeera, accessing specially protected material, according to a document dated in 2006.[67]
- The NSA hacked the French Foreign Ministry, and bugged the French diplomatic offices in Washington and New York in 2010.[178]
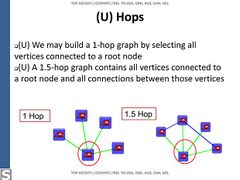
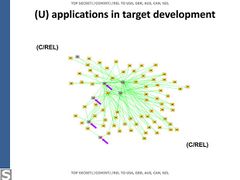
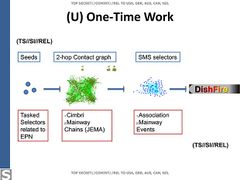
- The NSA conducted extensive spying on Enrique Peña Nieto, and his aides, accessing their emails. Likewise, the NSA spied on the communications of Dilma Rousseff, and her aides, and also created a two hop contact graph. The source document is dated June 2012, it is unclear whether the operation is ongoing.[193][194][195]
- The NSA and GCHQ target banks and credit card companies by various means including "Tailored Access Operations", specifically by targeting printer traffic from banks. VISA has also been targeted. According to a GCHQ document, the collection involves "bulk data" containing "rich personal information" that is mostly "not about our targets".[177]
- From collection points outside the United States, the NSA gathers contact lists belonging to users of e-mail and instant messaging services, including Yahoo, Hotmail, Facebook and Gmail.[196]
علاقات وكالة الأمن القومي بالمخابرات الأجنبية
- Payments to GCHQ from NSA totaling at least £100 million
- Relationships with Germany's BND, exchange of technology: (XKeyscore, and the German programs and bulk metadata (500 Million records in one month alone)).
- The US directly spies on most of its allies, even those with intelligence sharing agreements, with only the Five Eyes being immune.[148]
المعايير المقترحة للحماية من التجسس
التعمية
In cryptography, encryption is the process of encoding information in such a way that eavesdroppers or hackers cannot read it, but that authorized parties can. According to Snowden's recommendations published by The Guardian Edward in September 2013 ,[197] properly implemented strong crypto systems were among the few things which one can rely on. However, endpoint security is often too weak to prevent the NSA from finding ways around it.[197]
مخابئ تحت الأرض
In September 2013, it was reported by the press that a number of countries deemed by the US and its allies to be rogue states, such as Syria, Iran and North Korea, had successfully evaded U.S. government surveillance by constructing secret bunkers deep below the Earth's surface.[198]
China's underground megaproject, the 816 Nuclear Military Plant in Chongqing (now declassified and opened to tourists), was reported to be "most worrying" for the U.S. Defense Intelligence Agency.[198]
Libya evaded surveillance by building "hardened and buried" bunkers at least 40 feet below ground level.[198]
غير مرتبطة بإدوارد سنودن
- In 2002, the NSA, in cooperation with the FBI, and in cooperation with Qwest, monitored nearly all communications in the Salt Lake area in the six months surrounding the Olympic games.[166][199][200]
- Since 2005, Canada has been running a bulk phone metadata, email and text message program.[201][202][203]
- The NYPD is engaging in mass surveillance, particularly of Muslims, in mosques, in social gatherings, and even at home. The department employs "rakers" to troll Muslim neighborhoods. The unit employing said rakers, was once called "The Demographics Unit," the name was changed in 2010 to the "Zone Assessment Unit" to mask the appearance, though not change the actual fact of racial profiling. Knowledge of this program was kept from the city council.[204]
- Devices made by the American company Blue Coat Systems, which are used for Internet surveillance and censorship, have turned up repeatedly in countries that censor and surveil the Internet, and have a record of human rights abuses, such as Iran, Syria, China, Burma (Myanmar) and Sudan.[205][206][207][208]
- The ACLU has released a report on the proliferation of license plate readers and on the retention of data from them.[209][210]
- The FBI has been pressuring ISPs to install surveillance software, referred to as the "harvesting program".[211]
- The FBI has been using malware and hacking to surveil suspects. Reports indicate however, that hacking and malware usage remains a last resort, and that warrants are sought for individual cases.[212][213]
- The NSA collects the contents of emails that transit from the US to abroad, and searches them for keywords.[214]
- The Post Office scans all envelopes, outsides of packages and postcards.[215]
- France's Equivalent of PRISM
- India will be building a mass domestic surveillance program called the "Central Monitoring System", which will be able to track all voice, fax, and text across all telephone networks in the country. It will also contract the Israeli company Verint Systems to monitor encrypted Gmail, BlackBerry, Skype and Yahoo! mail.[216][217]
- More than 230 thousand people were questioned under The United Kingdom's Schedule 7 of the Terrorism act of 2000 between April 2009 and March 2012.[218]
- New Zealand passed a bill allowing domestic spying against its citizens and residents, by a narrow margin (61–59).[219][220]
- Russ Tice, on 19 June gave an interview to Boiling Frogs Post, in which he expanded his previous disclosures. Specifically he names persons who had been wiretapped by the NSA, namely: Hillary Clinton, Barack Obama, Diane Feinstein, Colin Powell, Evan Bayh, Samuel Alito and many others including journalists and political groups. He asserts that all telephony content is collected.[221]
- Blueprints of the Utah Data Center[222]
- "The Find," the NSA can locate even unpowered cellphones.[223]
- The DEA's and IRS's use of NSA data to start criminal investigations against US citizens, and their method of "Parallel Construction" to conceal the true origins of their evidence.[224][225]
- CIA operative De Sousa, convicted in absentia in Italy in the extraordinary rendition case of Osama Mustapha Hassan Nasr AKA Abu Omar goes on camera describing the case.[226]
- Insider Threat Program – policy requiring federal employees to report "high-risk persons or behaviors" from among co-workers, as well as to punish those who fail to report such colleagues.[227] In 2013, the NSA planned to investigate over 4000 cases.[81]
- The German Federal Office for Information Security has warned that Windows 8 has a built-in backdoor, that could allow Microsoft, and by extension the NSA to access many Windows 8 machines via the Trusted Platform Module that comes embedded on many Windows 8 machines.[228][229] Of the subset of CIA applicants whose backgrounds raised flags, one fifth were found to have ties to either terrorism or foreign hostile intelligence.[230]
- The NSA has admitted about a dozen cases of willful violations by analysts over the last 10 years.[231] One common form, in which an analyst spies on a love interest, has been dubbed "LOVEINT"[232]
- The Hemisphere Project, a secret partnership between federal and local drug officials and AT&T since September 2007. Law enforcement has access to electronic call detail records for any telephone carrier that uses an AT&T switch to process a telephone call. Records go back to 1987 and about 4 billion are added every day. Officials are instructed to obfuscate the existence of the program, by a method similar to "Parallel Construction" in which a separate subpoena is obtained for records which had already been returned by the Hemisphere project, thus disguising the true origin of the data.[233][234]
- Sweden is helping the GCHQ tap fiber-optic cables and has become, effectively, a member of the 'Five Eyes', according to Duncan Campbell in a hearing of the EU parliament's LIBE committee. He further states that the codename for the tapping operation is "Sardine" and is classified several levels above top secret, and that the information about Sweden was withheld from publication in the Guardian, The New York Times, and Pro Publica.[235][236][237]
- CIA, BND and the Federal Office for the Protection of the Constitution ran Projekt 6 (P6 for short) from 2005 to 2010. It's aim was to gather intelligence on suspected jihadists and terrorism supporters. An American query request for the internal database, code name PX contains the passport number, date of birth and name of German investigative journalist Peter Buchen.[238]
- The ACLU released a 69 page report on the FBI entitled "Unleashed and Unaccountable" detailing warrantless wiretapping, spying on political activists and journalists, biased training and racial profiling, proxy detentions in foreign countries, use of the no-fly list as a means of pressuring people to becomes informants, bulk data collection (eGuardian and bulk telephony metadata), dodging oversight and misleading the public.[239][240]
- The NSA purchases zero-day exploits from Vupen, as revealed in a FOIA request. In response, the CEO of Vupen suggested that a FOIA request also be made for Raytheon, Lockheed Martin and Northrop, because they also sell exploits.[241]
تقارير الإعلام
تأريخ

In April 2012, Snowden began downloading sensitive NSA material while working for the American computer corporation Dell Inc..[243]
By the end of 2012, Snowden had made his first contact with journalist Glenn Greenwald of The Guardian.[244] In January 2013, Snowden contacted documentary filmmaker Laura Poitras.[245]
In March 2013, Snowden took up a new job at Booz Allen Hamilton in Hawaii, specifically to gain access to additional top-secret documents that could be leaked.[243] In April 2013, Poitras asked Greenwald to meet her in New York City.[244]
In May 2013, Snowden was permitted temporary leave from his position at the NSA in Hawaii, on the pretext of receiving treatment for his epilepsy.[246]
On 20 May 2013, Snowden flew to Hong Kong.[247]
After The Guardian's editor held several meetings in New York City, it was decided that Greenwald, Poitras and "veteran" reporter Ewen MacAskill would fly to Hong Kong to meet Snowden. On 6 June 2013, the first media disclosure was published simultaneously by Greenwald (The Guardian) and Poitras (The Washington Post).[242][248]
In October 2013 The Guardian revealed that the NSA had been monitoring telephone conversations of 35 world leaders after being given the numbers by an official in another US government department. A confidential memo revealed that the NSA encouraged senior officials in such Departments as the White House, State and The Pentagon, to share their "Rolodexes" so the agency could add the telephone numbers of leading foreign politicians to their surveillance systems. Reacting to the news, German leader Angela Merkel, arriving in Brussels for an EU summit, accused the US of a breach of trust, saying: "We need to have trust in our allies and partners, and this must now be established once again. I repeat that spying among friends is not at all acceptable against anyone, and that goes for every citizen in Germany."[249]
الكشف
| الوسيلة الإخبارية | نوع الإعلام | ملخص الكشف |
|---|---|---|
| گارديان | صحيفة يومية بريطانية | The Guardian and the Washington Post both reported that the U.S. National Security Agency (NSA) has been monitoring Internet traffic in realtime via PRISM.[250][251] In addition, the Guardian reported that:
|
| واشنطن پوست | صحيفة يومية أمريكية | PRISM revelation, simultaneously with The Guardian.[223][267]
|
| والت ستريت جورنال | صحيفة يومية دولية أمريكية |
|
| نيويورك تايمز | صحيفة يومية دولية أمريكية |
|
| بلومبرگ نيوز | وكالة إخبارية دولية أمريكية | |
| ساوث شاينا مورنينگ پوست | صحيفة باللغة الإنگليزية مقرها هونگ كون | During specific episodes within a four-year period, the NSA hacked:
|
| در شپيگل | مجلة إخبارية ألمانية | Documents provided by Edward Snowden and seen by Der Spiegel revealed that the NSA spied on various diplomatic missions of the European Union (EU), including:
Only Australia, Canada, New Zealand and the UK are explicitly exempted from NSA attacks, whose main target in the EU is Germany.[300] Snowden also confirmed that Stuxnet was cooperatively developed by the United States and Israel.[301] The NSA gave the German intelligence agencies BND and BfV access to X-Keyscore.[94] In return, the BND turned over copies of two systems named Mira4 and Veras, reported to exceed the NSA's SIGINT capabilities in certain areas.[93] The NSA also provided the BND with analysis tools so that the BND can monitor foreign data streams flowing through Germany.[302][303] The BND is providing the NSA metadata collected from German systems. In December 2012 alone, Germany provided the NSA with 500 million metadata records.[304][305][306] The US runs a top-secret surveillance program, code name Special Collection Service, based in over 80 consulates and embassies worldwide, including Frankfurt Germany and Vienna, Austria.[90] The NSA hacked the United Nations' video conferencing system in Summer 2012 in violation of a UN agreement.[90] The NSA spied on the EU embassies in New York and Washington, code names Apalachee and Magothy. It deployed listening devices, copied hard drives and hacked internal networks.[90] The NSA spied on the Al Jazeera and gained access to its internal communications systems.[307] A NSA branch called "Follow the Money" (FTM) widely monitors international payments, banking and credit card transactions and later stores the collected data in the NSA's own financial databank "Tracfin".[308] The NSA monitored the president's public email account of former Mexican president Felipe Calderón (thus gaining access to the communications of high ranking cabinet members), the E-Mails of several high-ranking members of Mexico's security forces and text and the mobile phone communication of current Mexican president Enrique Peña Nieto.[309][310] The mobile phone of German Chancellor Angela Merkel might have been tapped by US intelligence.[311][312][313][314][315][316] According to the Spiegel this monitoring goes back to 2002,[317][318][319] while the New York Times reported that Germany has evidence that the NSA's surveillance of Merkel began during George W. Bush's tenure.[320] |
| او گلوبو وشبكة گلوبو | صحيفة برازيلية، وشبكة تلفزيونية |
|
| سيدني مورنينگ هرالد | صحيفة أسترالية | British Government Communications Headquarters is collecting all data transmitted to and from the United Kingdom and Northern Europe via the undersea fibre optic telecommunications cable SEA-ME-WE 3. Singaporean intelligence co-operates with Australia in accessing and sharing communications carried by the SEA-ME-WE-3 cable. The Australian Signals Directorate, is also in a partnership with British, American and Singaporean intelligence agencies to tap undersea fibre optic telecommunications cables that link Asia, the Middle East and Europe and carry much of Australia's international phone and internet traffic.[100] |
| إيه بين سي نيوز (أستراليا) | خدمة إخبارية أسترالية | * The Australian Federal Government knew about the internet spying program PRISM months before Edward Snowden made details public.[329][330] |
| Süddeutsche Zeitung | صحيفة ألمانية | Documents leaked by Edward Snowden and jointly disclosed by Süddeutsche Zeitung (SZ) and Norddeutscher Rundfunk revealed that several telecom operators have played a key role in helping the British intelligence agency Government Communications Headquarters (GCHQ) tap onto worldwide fiber-optic communications.[331][332] The telecom operators are:
Each of them were assigned a particular area of the international fiber-optic network for which they were individually responsible. The following networks have been infiltrated by the GCHQ:
Telecommunication companies who participated were "forced" to do so and had "no choice in the matter".[103] Some of the companies were subsequently paid by GCHQ for their participation in the infiltration of the cables.[334] According to the SZ the GCHQ has access to the majority of internet and telephone communications flowing throughout Europe, can listen to phone calls, read emails and text messages, see which websites internet users from all around the world are visiting.[333] It can also retain and analyse nearly the entire european internet traffic.[332]
|
| Norddeutscher Rundfunk | خدمة بث عام | |
| Pro Publica, The Guardian and The New York Times | independent journalists; British and American daily newspapers | The Guardian and the New York Times reported on secret documents leaked by Snowden showing that the NSA has been in "collaboration with technology companies" as part of "an aggressive, multipronged effort" to weaken the encryption used in commercial software, that the GCHQ has a team dedicated to cracking "Hotmail, Google, Yahoo and Facebook" traffic, and other revelations.[162][339][340][341][342][343] |
| لوموند | صحيفة يومية فرنسية | * The NSA targeted in France both people suspected of association with terrorist activities as well as people belonging to the worlds of business, politics or French state administration. The NSA monitored and recorded the content of telephone communications and the history of the connections of each target i.e. the metadata.[344][345] |
التداعيات
Shortly after the disclosures were published, US President Barack Obama asserted that the American public had no cause for concern because "nobody is listening to your telephone calls",[347] and "there is no spying on Americans".[348]
On 21 June 2013, the Director of National Intelligence James R. Clapper issued an apology for giving false testimony under oath to the United States Congress, which is a felony under 18 USC s. 1001. Earlier in March that year, Clapper was asked by Senator Ron Wyden to clarify the alleged surveillance of U.S. citizens by the NSA:
Senator Wyden: "Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?"
Director Clapper: "No, Sir."[349]
In an interview shortly after Snowden's disclosures were first published, Clapper stated that he had misunderstood Wyden's question and answered in what he thought was the "least untruthful manner".[350] Later, in his letter of apology, Clapper wrote that he had only focused on Section 702 of the Foreign Intelligence Surveillance Act during his testimony to Congress, and therefore, he "simply didn't think" about Section 215 of the Patriot Act, which justifies the mass collection of telephone data from U.S. citizens.[351] Clapper said: "My response was clearly erroneous—for which I apologize".[351]
To increase transparency and because it is in the public interest the Director of National Intelligence authorized the declassification and public release of the following documents pertaining to the collection of telephone metadata pursuant to Section 215 of the PATRIOT Act on 31 July 2013.[352] These documents were:
- Cover Letter and 2009 Report on the National Security Agency’s Bulk Collection Program for USA PATRIOT Act Reauthorization[353]
- Cover Letters and 2011 Report on the National Security Agency's Bulk Collection Program for USA PATRIOT Act Reauthorization[354]
- Primary Order for Business Records Collection Under Section 215 of the USA PATRIOT Act[355]
In a press conference on 9 August 2013 President Obama announced four steps to reform U.S. intelligence gathering measures, to increase transparency and restore public trust in surveillance by NSA, but made no indication to alter the NSA's ongoing mass collection of phone data and surveillance of internet communications in the short term.[356][357] These four steps are:[358][359][360]
- Reform Section 215 of the Patriot Act which allows the National Security Agency to collect telephone data from millions of communications without a warrant.[358]
- More transparency: Declassification of the legal rationale for the US government's phone-data collection,[171][361][362][363] release of NSA information that details its mission, authorities, and oversight,[170][171][364] installation of a "civil liberties and privacy officer" at the National Security and a website created by the American intelligence community to inform Americans and the world what the intelligence community does and what it doesn’t do, how it carries out its mission, and why it does so.[358]
- More balance between security and privacy at the Federal Intelligence Surveillance Court by appointing an adversarial voice – such as a lawyer assigned to advocate privacy rights[365] – to argue against the US government to ensure to make sure civil liberties concerns have an independent voice in appropriate cases.[358]
- Review of all US government intelligence and communications technologies by a group of external experts (composed of former intelligence officials, civil liberties and privacy advocates, and others)[365] which shall provide an interim report in 60 days and a final report by the end of 2014 outlining how the US government can maintain the trust of the people, how it can make sure that there absolutely is no abuse in terms of how surveillance technologies are used and how surveillance impacts US foreign policy.[358] Director of National Intelligence James R. Clapper has been directed on 13 August 2013 to form and review the new Review Group on Intelligence and Communications Technologies, which is to brief Obama on its interim findings within 60 days of the establishment of the group. A final report and recommendations are to be submitted through Clapper to the president no later than 15 December 2013.[364][366][367] The group's purpose is to assess whether the US "employs its technical collection capabilities in a manner that optimally protects our national security and advances our foreign policy while appropriately accounting for other policy considerations, such as the risk of unauthorized disclosure and our need to maintain the public trust."[368]
In a reaction to Obama above reform proposals responsible for overseeing the program which collects Americans’ telephone communications data in bulk say that they felt in recent years limited in their ability to challenge its scope and legality. They pointed out to intelligence officials who would not volunteer details if questions were not asked with absolute precision in regular meetings; hearing only from government officials steeped in the legal and national security arguments for aggressive spying; and House members must rely on the existing committee staff, many of whom used to work for the spy agencies they are tasked with overseeing, while Senate Intelligence Committee members can each designate a full-time staffer for the committee who has full access. Additional obstacles stemmed from the classified nature of documents, which lawmakers may read only in specific, secure offices; rules require them to leave their notes behind and restrict their ability to discuss the issues with colleagues, outside experts or their own staff.[369]
On 12 August 2013, President Obama announced the creation of an "independent" panel of "outside experts" to review the NSA's surveillance programs. The panel is due to be established by the Director of National Intelligence, James R. Clapper, who will consult and provide assistance to them.[370] The "independent" panel of "outside experts" is composed of intelligence insiders, former White House officials and Obama advisers, who did not discuss any changes to the National Security Agency's controversial activities at its first meeting.[371]
On 19 July 2013, Human Rights Watch sent a letter to the Obama administration, urging it to allow companies involved in the NSA's surveillance to report about these activities and to increase government transparency.[372]
On 18 August 2013, Amnesty International asserted that if journalists maintain their independence and report critically about governments, they too may be "targeted" by the British government.[373]
On 20 August 2013, Index on Censorship argued that the British government's "threat of legal action" against The Guardian was a "direct attack on press freedom in the UK".[374]
On 4 September 2013, U.N. Special Rapporteur Frank La Rue stressed that the "protection of national security secrets must never be used as an excuse to intimidate the press into silence."[375]
محاولات الحد من الأضرار المتصورة
- Press censorship: British government officials issued a confidential DA-Notice to several press organizations, with the aim of restricting their ability to report on these leaks.[376] According to the U.S. Army, its decision to block The Guardian website was based upon the need to prevent service personnel from accessing press coverage and online content related to these disclosures.[377]
- Detention without charge: On 18 August 2013, David Miranda, partner of journalist Glenn Greenwald, was detained under Schedule 7 of the United Kingdom's Terrorism Act of 2000. Miranda was returning from Berlin, carrying 58,000 GCHQ documents on a single computer file[378] to Greenwald in Brazil. Greenwald described Miranda's detention as "clearly intended to send a message of intimidation to those of us who have been reporting on the NSA and GCHQ".[379][380][381][382] The Metropolitan Police and Home Secretary Teresa May argued that Miranda's detention "legally and procedurally sound".[383] However, Lord Falconer of Thoroton, responsible for introducing the bill in the House of Lords, said that under the act, police can only detain someone "to assess whether they are involved in the commission, preparation or instigation of terrorism". He said "I am very clear that this does not apply, either on its terms or in its spirit, to Mr Miranda."[384] Antonio Patriota the Brazilian Minister of External Relations said that Miranda's detention was "not justifiable". The reasons for Miranda's detention were sought from the police by British politicians and David Anderson QC, the independent reviewer of terrorism legislation.[385] The United States government later said that British officials had given them a "heads up" about Miranda's detention, while adding that the decision to detain him had been a British one.[385]
- Destruction of evidence: Guardian editor Alan Rusbridger said the newspaper had received legal threats from the British government and was urged to surrender all documents leaked by Snowden. Security officials from the Government Communications Headquarters (GCHQ) later made a visit to the newspaper's London headquarters to ensure that all computer hard drives containing Snowden's documents were destroyed.[383][386]
- Editing of interview transcript: After the NSA Director of Compliance John Delong was interviewed by The Washington Post regarding these disclosures, the White House sent a "prepared" statement to The Post and ordered that "none of Delong's comments could be quoted on the record". The Post refused to comply.[387][388]
- Forced landing of Morales' plane: Five Latin American countries – Bolivia, Cuba, Ecuador, Nicaragua and Venezuela – voiced their concerns to the UN Secretary-General Ban Ki-Moon after the plane of Bolivia's President Evo Morales was denied entry by a number of western European countries, and was forced to reroute to Austria based on "suspicion that United States whistleblower Edward Snowden was on board".[389] Ban said it was important to prevent such incidents from occurring in the future and emphasized that "A Head of State and his or her aircraft enjoy immunity and inviolability".[389]
محاولات الكونگرس الأمريكي تقويض وكالة الأمن القومي
كاستجابة للمعلومات التي سربها سنودن، الممثل جسنين أماش (ج.ميچ.) والممثل جون كونيرس (د.ر) قدما "تعديل أماش-كويرز" على قانون سلطة الدفاع القومي.[390] إذا ما تم التصديق عليه، فسيقلص التعديل "الجمع المستمر وتخزين السجلات الشخصية للأمريكيين الأبرياء". رفض المجلس هذا التعديل بتصويت 205–217.[391] في تحليل يشير إلى أن من صوتوا ضد التعديل حصلوا على أكثر من 122% في اسهامات الحملة من مقاولي الدفاع عن من صوتوا لصالحه.[392]
في سبتمبر 2013، السناتور مارك اودال، ريتشارد بلومنتال، راند پول ورون ويدن، قدمو مقترح "اصلاح التجسس الشامل".[393] والذي يعتبر الاقتراح الأكثر شمولاً حتى الآن، "قانون المراقبة الاستخباراتية واصلاح التجسس" يطالب بوضع نهاية للمجموعة الهائلة لسجلات الاتصالات والتي تمت بطريقة غير قانونية بموجب البند 215 من القانون الوطني وغلبت على معظم "برامج التجسس الإلكتروني" الأخرى.[394] صرح ويدن للگارديان بأن تسريبات سنودن "تسببت في تغير جذري للطريقة التي ينظر بها العامة لنظام المراقبة". مسودة القانون تدمج بين 12 مقترح مشابه بالإضافة إلى مقترحات تشريعية.[395]
التأثير على العلاقات الخارجية
تسببت التسريبات الإعلامية بتوتر في العلاقات الثنائية الأمريكية مع مخلف حلفائها وشركائها الاقتصاديين وكذلك في علاقتها مع الاتحاد الاوروپي:
عبرت الحكومة البرازيلية عن غضبها لاكتشاف أن وكالة الأمن القومي استهدفت بشكل مباشر اتصالات الرئيسة ديلما روسف وكبار مساعديها.[325] وقالت عل الحادث أنه "انتهاك غير مقبول للسيادة" وطلبت بتفسير فوري من الحكومة الأمريكية.[396]
أشارت الحكومة البرازيلية إلى إلغاء الزيارة الرسمية لروسف إلى واشنطن - الزيارة الرسمية الوحيدة التي كانت مجدولة لقائد أجنبي في تلك السنة.[397] أعلن مسئول برازيلي رفيع المستوى أن بلاده ستخفض من الروابط التجارية حتى تتلقى روسف اعتذار علني.[397] ويشمل ذلك استبعاد 4 بليون دولار قيمة شراء مقاتلات بوينگ إف-18 سوپر هورنت والتعاون في مجال تكنولوجيا النفط والوقود الحيوي، بالإضافة إلى اتفاقيات تجارية أخرى.[397]
حسب هوانگ چنشگچينگ، مدير فريق طوارئ الحاسوب الصيني، أن حوالي 2.91 مليون حاسوب رئيسي في الصين تم اختراقه من أكثر من 4.000 خادم مقره الولايات المتحدة.[398] في 17 يونيو 2013، بعد أسبوعين من نشر أول تسريب، صرح المتحدث الرسمي باسم وزارة الخارجية الصينية:
"نعتقد أن على الولايات المتحدة أن تهتم بمخاوف المجتمع الدولي ومطالبه وتقدم له التفسير اللازم"[399]
في 21 أكتوبر 2013، استدعت فرنسا تشارلز ريڤكين، السفير الأمريكي في فرنسا، لتقديم توضيح وتفسير حول تجسس وكالة الأمن القومي على المواطنين الفرنسيين.[400] في حديث أدلى به الرئيس الفرنسي فرانسوا اولاند للصحفيين في ميناء لوريان الفرنسي، قال:
"لا يمكنا قبول سلوك من هذا النوع بين شركاء وحلفاء.. نحن نطالب بالتوقف عن هذا فوراً."[401]
في 1 يوليو 2013، استدعت وزارة الخارجية الألمانية فليپ د. مرفي، السفير الأمريكي في ألمانيا، بخصوص مزاعم تجسس وكالة الأمن القومي على مؤسسات الاتحاد الاوروپي.[402] في 24 أكتوبر 2013، استدعى وزير الخارجية جون ب. إمرسون، السفير الأمريكي في ألمانيا، لتفسير مزعم تصنت وكالة الأمن القومي على الهاتف المحمول للمستشارة أنگلا مركل،.[403][404]
في أوائل أغسطس 2013، ألغيت الاتفاقيات الادارية الشكلية في فترة الحرب الباردة مع بريطانيا، الولايات المتحدة وفرنسا، والتي كانت تمنح البلدان الغربية والتي كان جنودها يتمركزون في ألمانيا الغربية، بحق القيام بعمليات تجسس لحماية قواتها.[405]
في نهاية أغسطس 2013، بأوامر من وكالة المخابرات المحلية الألمانية، رصدت مروحية شرطة فدارية على مستوى منخفض فوق القنصلية الأمريكية في فرانكفورت، يشتبه في أنها كانت تبحث عن مرافق في التصنت عليها سراً. أطلق المسئولون الألمان على هذا أنه "طلقة تحذيرية" رمزية.[406]
طلب رئيس الوزراء الإيطالي إنريكو ليتا من جون كري، وزير الخارجية الأمريكي، توضيح ما إذا كانت وكالة الأمن القومي قامت باعتراض غير قانوني للاتصالات في إيطاليا.[407] في 23 أكتوبر 2013، قام وزير الداخلية الإيطالي أنگلينو ألفانو بتصريح صحفي في روما:
"نحن مسئولون عن (توفير) توضيح للمواطنين الإيطاليين - يجب أن نعرف الحقيقة كاملة ونقول الحقيقة كاملة، دون اعتبار لأحد."[408]
في 24 أكتوبر 2013، التقى وزير الخارجية المكسيكي خوسيه أنطونيو مياده كوريبرنا مع السفير الأمريكي إيرل أنطوني واين لتوضيح تفاصيل الوثائق التي سربها سنودن.[409]
في 25 أكتوبر 2013، استدعى رئيس الوزراء الإسپاني ماريانو راخوي جيمس كوستوس، السفير الأمريكي في إسپنيا، لتقديم تفسير حول تجاسس وكالة الأمن القومي على الحكومة الإسپانية.[410] وزير الاتحاد الاوروپي الإسپاني، إنيگو مندز ده ڤيگو، صرح بأن مثل هذه الممارسات، لو كانت صحيحة، ستكون "غير لاقئة وغير مقبولة". كان ممثل الاتحاد الاوروپي قد التقى بمسئولين في واشنطن لإبلاغهم قلق بلاده.[411]
في أوائل يوليو 2013، كتبت المفوضة الاوروپية لشؤون الوطن، سسيليا مالمستروم، إلى إثنين من المسئولين الأمريكيين بأن "الثقة والمصداقية المتبادلة قد اهتزت، وأنا اتوقع من الولايات المتحدة أن تفعل ما بوسعها لاستعادتها".[412]
في 20 أكتوبر 2013، دعمت لجنة في الپرلمان الاوروپي معيار، بأنه إذا ما تم سنه، فيستطلب من الشركات الأمريكية طلب تصريح من المسئولين الاوروپيين قبل الامتثال لأوامر الولايات المتحدة بالحصول على بيانات خاصة. استمر هذا التشريع تحت الدراسة لسنتين. كان التصويت جزء من جهود اوروپا لحماية مواطنيها من التجسس اونلاين في أعقاب الكشف عن برامج تجسس واسعة النطاق تديرها وكالة الأمن القومي.[413]
في لقاء عقده المجلس الاوروپي في نهاية أكتوبر 2013 وفي بيانه الذي وقع عليها جميع القادة الاوروپيين ال28 والذي يشدد على أن "جمع المعلومات الاستخبارية هو عنصر حيوي في الحرب ضد الإرهاب" وشدد على "العلاقة الوثيقة بين اوروپا والولايات المتحدة وقيمة هذه الشراكة"، وقال أن هذا يجب أن "يعتمد على الاحترام والثقة"، وفقدانها "التعاون اللازم في مجال جمع المعلومات الاسختباراتية".[414][415]
التأثير على التجارة
بدا من الملاحظ حدوث ركود في مستلزمات الحاسوب والبرمجيات التحليلية في السوق الصيني. [2] ويعزى ذلك إلى الوثائق التي سربها سنودن، وليس لحالة السوق.
العواقب المتصورة على مكافحة الارهاب والأمن القومي
Late June 2013, Keith B. Alexander, the director of the NSA, asserted that these media leaks had caused "significant" and "irreversible" damage to the national security of the United States and this "irresponsible" release of classified information will have a "long-term detrimental" impact on the intelligence community's ability to detect future attacks. Furthermore, these leaks have "inflamed and sensationalized" the work that the intelligence community does lawfully under "strict oversight and compliance".[416]
In early October 2013, former GCHQ director Sir David Omand, speaking of how useful for Russia's intelligece services Snowden's stay in Russia could be, told the BBC: "Part of me says that not even the KGB in its heyday of Philby, Burgess and Maclean in the 1950s could have dreamt of acquiring 58,000 highly classified intelligence documents."[417] Snowden stated that he had not leaked any documents to Russia.[418]
Andrew Parker, the director general of the UK Security Service maintained in October 2013 that the exposing of intelligence techniques had given extremists the ability to evade the intelligence agencies; he said,"It causes enormous damage to make public the reach and limits of GCHQ techniques. Such information hands the advantage to the terrorists. It is the gift they need to evade us and strike at will."[419]
Shortly afterwards, The Financial Times editorialised that security chiefs were "right to be alarmed, knowing that terrorists can change their modus operandi in response to new information on their capabilities" and there was "no firm evidence that the intelligence agencies are using these new collection capabilities for malign ends."[378]
ردود الفعل
الولايات المتحدة
السلطة التنفيذية
In early June 2013, the U.S. Director of National Intelligence, James R. Clapper, referring to the surveillance activities reported in The Washington Post and Guardian shortly prior, stressed that those were lawful and conducted under authorities approved by the US Congress and that "significant misimpressions" had resulted from those articles; he called the disclosures of "intelligence community measures used to keep Americans safe" "reckless".[420] He condemned the leaks as having done "huge, grave damage" to the U.S. intelligence capabilities.[421] The NSA formally requested that the Department of Justice launch a criminal investigation into Snowden's actions.[420]
On June 14, 2013, US federal prosecutors filed a sealed complaint, made public on June 21,[422] charging Snowden with theft of government property, unauthorized communication of national defense information, and willful communication of classified intelligence to an unauthorized person; the latter two charges being under the Espionage Act.[423]
In June 2013, the U.S. military blocked access to parts of the Guardian website related to government surveillance programs for thousands of defense personnel across the country, and to the entire Guardian website for personnel stationed in Afghanistan, the Middle East, and South Asia.[424][425] A spokesperson described the filtering as a routine "network hygiene" measure intended to mitigate unauthorized disclosures of classified information onto the Department of Defense's [DOD] unclassified networks.[424]
On Sunday, August 4, Chairman of the Joint Chiefs of Staff Martin Dempsey was shown on the weekly ABC interview show This Week saying that Snowden "has caused us some considerable damage to our intelligence architecture. Our adversaries are changing the way that they communicate."[426]
United States President Barack Obama was dismissive of Snowden in late June, saying, "I'm not going to be scrambling jets to get a 29-year-old hacker."[427][428] In early August, Obama said that Snowden was no patriot and that Americans would have been better off if they had remained unaware of the NSA surveillance activities that Snowden revealed.[429] Obama also said that he had "called for a thorough review of our surveillance operations before Mr. Snowden made these leaks.... My preference, and I think the American people's preference, would have been for a lawful, orderly examination of these laws; a thoughtful fact-based debate that would then lead us to a better place."[429] On August 9, Obama announced that he was ordering Director of National Intelligence James Clapper to arrange for "a high-level group of outside experts to review our entire intelligence and communications technologies.”[430][431] Director of National Intelligence James Clapper acknowledged that Snowden may have done a public service and started a needed debate about the balance between privacy and security. “As loath as I am to give any credit for what’s happened here, which was egregious, I think it’s clear that some of the conversations that this has generated, some of the debate, actually probably needed to happen,” he said, “It’s unfortunate they didn’t happen some time ago, but if there’s a good side to this, that’s it.”[432][433]
الكونگرس
Reactions to Snowden's disclosures among members of Congress initially were largely negative.[434] Speaker of the House John Boehner[435] and senators Dianne Feinstein[436] and Bill Nelson[437] called Snowden a traitor, and several senators and representatives joined them in calling for Snowden's arrest and prosecution.[436][438][439]
Representative Thomas Massie was one of few members of Congress to question the constitutional validity of the government surveillance programs and suggest that Snowden should be granted immunity from prosecution.[440] Senators Ted Cruz[441] and Rand Paul[442] offered tentative support for Snowden, saying they were reserving judgment on Snowden until more information about the surveillance programs and about Snowden's motives were known. Senator Paul said, "I do think when history looks at this, they are going to contrast the behavior of James Clapper, our National Intelligence Director, with Edward Snowden. Mr. Clapper lied in Congress in defiance of the law, in the name of security. Mr. Snowden told the truth in the name of privacy."[443] Paul later called Snowden a "civil disobedient", like Martin Luther King Jr., but who faced life imprisonment.[444] Representative John Lewis made comparisons between Snowden and Gandhi, saying the leaker was appealing to a "higher law".[445]
Senator Bill Nelson, "What Edward Snowden did amounts to an act of treason."[446] Similar comments have also been made by Rep. Peter T. King, Rep. John Boehner, and Sen. Dianne Feinstein.[447]
On July 25, the US Senate Committee on Appropriations unanimously adopted an amendment by Senator Lindsey Graham to the "Fiscal Year 2014 Department of State, Foreign Operations, and Related Programs Appropriations Bill"[448] that would seek sanctions against any country that offers asylum to Snowden.[449][450][451]
In response to the information release by Snowden, Rep. Justin Amash (R-Mich.) and Rep. John Conyers (D-Mich.) proposed an amendment to the National Defense Authorization Act[452] to curtail the NSA gathering and storage of the personal records, but the House rejected it by a narrow margin of 205–217.[453] Amash subsequently told Fox News that Snowden was "a whistle-blower. He told us what we need to know."[454]
On the Sunday ABC interview show This Week, Rep. Dutch Ruppersberger, D-Maryland, of the United States House Select Committee on Intelligence was asked by Raddatz, "Are efforts being thwarted in trying to get information for members of Congress?" He replied,
"...[S]ince this incident occurred with Snowden, we've had three different hearings for members of our Democratic Caucus, and the Republican Caucus, where General Alexander has come with his deputy, Chris Inglis, to ask any questions that people have as it relates to this information. And we will continue to do that because what we're trying to do now is to get the American public to know more about what's going on....But we can do better. I have to educate my caucus more, the Democratic Caucus. And we're trying to declassify as much as we can."[455]
U.S. Senator John McCain (R-AZ) said on the August 11 edition of Fox News Sunday that Snowden had become a hero to young Americans, as he reminded them of the Jason Bourne character. McCain attributed it to generation change and a lack of confidence in the federal government. "Right now there's kind of a generational change," he said. "Young Americans do not trust this government."[456]
Gordon Humphrey, the conservative Republican senator for New Hampshire from 1979–1991, expressed support for Snowden.[457] Glenn Greenwald revealed that Humphrey, a former member of the Senate Foreign Relations Committee, had been in contact with Snowden via email. Humphrey told Snowden, "Provided you have not leaked information that would put in harms way any intelligence agent, I believe you have done the right thing in exposing what I regard as massive violation of the United States Constitution."[458] Humphrey cited Snowden as a "courageous whistle-blower".[459]
Tom McClintock (R-Calif) came out in favor of amnesty for Snowden, saying "I think it would be best if the American government granted him amnesty to get him back to America where he can answer questions without the threat of prosecution... We have some very good laws against sharing secrets and he broke those laws. On the other hand, he broke them for a very good reason because those laws were being used in direct contravention of our 4th Amendment rights as Americans."[460]
الرأي العام
Polls conducted by news organisations following Snowden's disclosures about government surveillance programs to the press indicated that American public opinion on Snowden's actions was divided. A Gallup poll conducted June 10–11, 2013 showed 44 percent of Americans thought it was right for Snowden to share the information with the press while 42 percent thought it was wrong.[461] A USA Today/Pew Research poll conducted June 12–16 found that 49 percent thought the release of information served the public interest while 44 percent thought it harmed it. The same poll found that 54 percent felt a criminal case should be brought against Snowden, while 38 percent thought one should not be brought,[462][463] while a Washington Post/ABC News poll conducted between the same dates as the Pew poll cited 43 percent of respondents saying Snowden ought to be charged with a crime, while 48 percent said he ought not.[464] Another poll in early July found 38 percent of Americans thought he did the wrong thing, 33 percent said he did the right thing, and 29 percent were unsure.[465] A WSJ/NBC poll conducted July 17–21 found that 11% of Americans viewed Snowden positively while 34% had a negative view.[466] A Quinnipiac University Polling Institute poll conducted June 28 – July 8 found that in the wake of Snowden's disclosures, more Americans said that government goes too far in restricting civil liberties as part of the war on terrorism (45 percent) than said that government does not go far enough to adequately protect the country (40 percent).[467] That finding was evidence of a massive swing in public opinion since an earlier Quinnipiac poll, conducted in 2010, when only 25 percent of respondents had said government goes too far in restricting civil liberties while 63 percent had said government does not go far enough. The same poll found that 55 percent of Americans regarded Snowden as a whistleblower while 34 percent saw him as a traitor.[467] Quinnipiac showed that a majority of Americans, by a wide margin, still regarded Snowden as a whistleblower rather than a traitor when it repeated the poll July 31 – August 1.[468]
After the June 2013 release, mass protests against government surveillance were reported in many parts of the world. In the United States, a political movement known as "Restore the Fourth" was formed and it gained momentum rapidly. In early July, Restore the Fourth was responsible for protests in more than 80 cities including Seattle, San Francisco, Denver, Chicago, Los Angeles and New York City. These protests were loosely coordinated via online messaging services and involved protestors from all over the United States.[469] Towards the end of July, it was reported in the media that the German intelligence agency BND had been actively cooperating with the NSA, which sparked demonstrations in 40 German cities involving thousands of protestors all over the country.[470]
On 26 October 2013, an anti-NSA rally in Washington, D.C. supported by a diverse coalition of over 100 advocacy groups attracted thousands of protestors calling for an end to mass surveillance.[471] Many marchers carried signs saying "Thank you, Edward Snowden". In a statement written by Snowden and read to the crowd, Snowden said, "This isn't about red or blue party lines, and it definitely isn't about terrorism. It's about being able to live in a free and open society."[472]
Glenn Greenwald, one of the journalists who received the documents, praised Snowden for having done a service by revealing the surveillance on the American public.[473][474] John Cassidy, also of The New Yorker, called Snowden "a hero", and said that "in revealing the colossal scale of the US government's eavesdropping on Americans and other people around the world, [Snowden] has performed a great public service that more than outweighs any breach of trust he may have committed."[475] CNN columnist Douglas Rushkoff also called Snowden's leak an act of heroism.[476] Amy Davidson, writing in The New Yorker, was thankful for the "overdue" conversation on privacy and the limits of domestic surveillance.[477]
American political commentators and public figures such as Noam Chomsky,[478] Chris Hedges,[479] Michael Moore,[480] Cornel West,[481] Glenn Beck,[480] Matt Drudge,[482] Alex Jones,[483] Andrew Napolitano,[484] Oliver Stone,[485] Michael Savage,[486] and Stephen Walt[487] praised Snowden for exposing secret government surveillance.
Other commentators were more critical of Snowden's methods and motivations.[488] Jeffrey Toobin, for example, denounced Snowden as "a grandiose narcissist who deserves to be in prison."[489] Writing in the The New Yorker, Toobin argued that the programs exposed were not illegal, therefore Snowden was not a whistleblower. Further, Toobin questioned "whether the government can function when all of its employees (and contractors) can take it upon themselves to sabotage the programs they don’t like".[489]
Former Vice President Dick Cheney, suggested in June 2013 that Snowden might be a spy working for the Chinese government.[490]
Stewart Baker, a former NSA general counsel in the early 1990s, said at a July 18, 2013 hearing, "I am afraid that hyped and distorted press reports orchestrated by Edward Snowden and his allies may cause us – or other nations – to construct new restraints on our intelligence gathering, restraints that will leave us vulnerable to another security disaster."[491]
Former CIA and NSA chief General Michael Hayden in late June 2013 welcomed the public debate about the balance between privacy and security that the leaks had provoked: "I am convinced the more the American people know exactly what it is we are doing in this balance between privacy and security, the more they know the more comfortable they will feel."[492][493] In September 2013, Hayden stressed the indisputable legality of "what the NSA is doing" and called Snowden a "troubled young man", albeit "morally arrogant to a tremendous degree"; he also said about his prospects in Russia: "I suspect he will end up like most of the rest of the defectors who went to the old الاتحاد السوڤيتي: Isolated, bored, lonely, depressed -- and most of them ended up alcoholics."[494]
Some former U.S. intelligence officials speculated that Chinese or Russian intelligence agents might have gleaned additional classified material from Snowden,[495][496][497] a view shared by some former Russian agents.[498] Snowden, however, told Greenwald in July that "I never gave any information to either government, and they never took anything from my laptops."[499]
In late June 2013, Former US President Jimmy Carter said: "He's obviously violated the laws of America, for which he's responsible, but I think the invasion of human rights and American privacy has gone too far ... I think that the secrecy that has been surrounding this invasion of privacy has been excessive, so I think that the bringing of it to the public notice has probably been, in the long term, beneficial."[500]
The editors of Bloomberg News argued that, while the government ought to prosecute Snowden, the media's focus on Snowden took attention away from issues of U.S. government surveillance, the interpretations of the Patriot Act, and the Foreign Intelligence Surveillance Act (FISA) court actions, all of which are "what really matters in all this."[501] Greenwald accused the media in the U.S. of focusing on Edward Snowden instead of on wrongdoing by Clapper and other U.S. officials.[502] In an op-ed, author Alex Berenson argued that the federal government should have flown a representative to Hong Kong to ask Snowden to give testimony in front of the U.S. Congress and offer him a fair criminal trial, with a view to preventing further unintended disclosures of classified information to other countries.[503]
On June 9, a We the People petition was launched on the whitehouse.gov website to seek "a full, free, and absolute pardon for any crimes [Snowden] has committed or may have committed related to blowing the whistle on secret NSA surveillance programs". The petition attained 100,000 signatures within two weeks, thus meeting the threshold and requiring an official response from the White House.[504] In October 2013, the Administration still had not responded to the petition, but gave no excuse for the four month delay.[505][506]
On August 8, 2013, Lavabit, a Texas-based secure email service provider reportedly used by Snowden, abruptly announced it was shutting down operations after nearly 10 years of business.[507] The owner, Ladar Levison, posted a statement online saying he would rather go out of business than "become complicit in crimes against the American people."[507] He also said that he was barred by law from disclosing what he had experienced over the preceding 6 weeks, and that he was appealing the case in the U.S. Fourth Circuit Court of Appeals.[507] Multiple sources speculated that the timing of the statement suggested that Lavabit had been targeted by the US government in its pursuit of information about Snowden.[507][508][509][510][511] The following day, a similar email service, Silent Circle, preemptively shut down in order to "prevent spying".[512] Snowden said about the Lavabit closure, "Ladar Levison and his team suspended the operations of their 10-year old business rather than violate the Constitutional rights of their roughly 400,000 users. The President, Congress, and the Courts have forgotten that the costs of bad policy are always borne by ordinary citizens, and it is our job to remind them that there are limits to what we will pay." He said that "internet titans" like Google should ask themselves why they weren't "fighting for our interests the same way small businesses are".[513]
اوروپا
الحكومات
British Foreign Minister William Hague admitted that Britain's GCHQ was also spying and collaborating with the NSA, and defended the two agencies' actions as "indispensable."[514][515][516] Meanwhile, UK Defence officials issued a confidential DA-Notice to British media asking for restraint in running further stories related to surveillance leaks including the PRISM programme and the British involvement therein.[517]
Documents from Snowden show that cooperation between Berlin and Washington in the area of digital surveillance and defense intensified considerably during time of Chancellor Merkel. The Bundesnachrichtendienst (BND), the foreign intelligence agency of Germany, is directly subordinated to the Chancellor's Office. Although Merkel denied knowing about surveillance, Germans take the claims seriously. According to Hansjörg Geiger, former head of the BND, findings/claims are Orwellian and mutual political and economic espionage would be explicitly forbidden.[518]
In the European Parliament, the Greens–European Free Alliance and European United Left–Nordic Green Left nominated Snowden for the 2013 Sakharov Prize for Freedom of Thought, which includes €50,000.[519][520]
الرأي العام
An opinion poll carried out by Emnid at the end of June revealed that 50% of Germans consider Snowden a hero, and 35% would hide him in their homes.[521]
Jürgen Trittin a German Green politician wrote in The Guardian Europe on July 2, 2013 "Edward Snowden has done us all a great service. The man who revealed that our US and UK allies are spying on us ought to be given refuge by an EU country. [...] If ever a case demonstrated why we need the protection of whistleblowers, this is it."[522]
المنظمات الغير حكومية

After Amnesty International met Edward Snowden in Moscow in mid July 2013, the organization said:
"What he has disclosed is patently in the public interest and as a whistleblower his actions were justified. He has exposed unlawful sweeping surveillance programmes that unquestionably interfere with an individual’s right to privacy. States that attempt to stop a person from revealing such unlawful behaviour are flouting international law. Freedom of expression is a fundamental right."[524]
Widney Brown, Senior Director of Amnesty, feared that Snowden would be at "great risk" of human rights violations if forcibly transferred to the United States,[525] and urged no country to return Snowden to the US. Michael Bochenek, Director of Law and Policy at Amnesty International deplored the US pressure on governments to block Snowden's asylum attempts, saying "It is his unassailable right, enshrined in international law".[526]
Human Rights Watch said that if Snowden were able to raise the issue of NSA mass surveillance without facing espionage charges, he would not have left the United States in the first place.[527] Human Rights Watch writes that any country where Snowden seeks asylum should consider his claim fairly and protect his rights under international law, which recognizes that revealing official secrets is sometimes justified in the public interest.[528]
Index on Censorship condemned the U.S. government for its "mass surveillance of citizens’ private communications" and urged all government officials to uphold the First Amendment to the United States Constitution. A statement released by Index on Censorship said: "Whistleblowers such as Edward Snowden — as well as journalists reporting on the Prism scandal, who have come under fire — should be protected under the first amendment, not criminalised."[529]
Navi Pillay, the United Nations High Commissioner for Human Rights, said: "Snowden's case has shown the need to protect persons disclosing information on matters that have implications for human rights, as well as the importance of ensuring respect for the right to privacy".[523]
Transparency International, International Association of Lawyers against Nuclear Arms and Vereinigung Deutscher Wissenschaftler awarded Snowden the German Whistleblowerpreis 2013.[530]
The Humanist Union awarded him the Fritz Bauer Prize 2013.[531]
الصين وهونگ كونگ
The South China Morning Post published a poll of Hong Kong residents conducted while Snowden was still in Hong Kong that showed that half of the 509 respondents believed the Chinese government should not surrender Snowden to the United States if Washington raises such a request; 33 percent of those polled think of Snowden as a hero, 12.8 percent described him as a traitor, 23 percent described him as "something in between."[532]
Referring to Snowden's presence in the territory, Hong Kong chief executive Leung Chun-Ying assured that the government would "handle the case of Mr Snowden in accordance with the laws and established procedures of Hong Kong [and] follow up on any incidents related to the privacy or other rights of the institutions or people in Hong Kong being violated."[533] Pan-democrat legislators Gary Fan and Claudia Mo said that the perceived U.S. prosecution against Snowden will set "a dangerous precedent and will likely be used to justify similar actions" by authoritarian governments.[534] During Snowden's stay, the two main political groups, the pan-democrats and Pro-Beijing camp, found rare agreement to support Snowden.[535][536] The pro-Beijing DAB party even organised a separate march to Government headquarters for Snowden.
The People's Daily and the Global Times editorials of June 19 stated respectively that the central Chinese government was unwilling to be involved in a "mess" caused by others, and that the Hong Kong government should follow the public opinion and not concern itself with Sino-US relations.[537] A Tsinghua University communications studies specialist, Liu Jianming, interpreted that the two articles as suggesting that the mainland government did not want further involvement in the case and that the Hong Kong government should handle it independently.[537]
After Snowden left Hong Kong, Chinese-language newspapers such as the Ming Pao and the Oriental Daily expressed relief that Hong Kong no longer had to shoulder the burden of the Snowden situation.[538] Mainland experts said that, although the Central Government did not want to appear to be intervening in the matter, it was inconceivable that the Hong Kong government acted independently in a matter that could have far-reaching consequences for Sino-US relations. One expert suggested that, by doing so, China had "returned the favor" for their not having accepted the asylum plea from Wang Lijun in February 2012.[539] The official Chinese Communist Party mouthpiece, the People's Daily denied the US government accusation that the PRC central government had allowed Snowden to escape, and said that Snowden helped in "tearing off Washington's sanctimonious mask."[540]
أمريكا الجنوبية
روبرت مندز، رئيس لجنة العلاقات الخارجية الأمريكية، حذر الإكوادور أن قبول سنودن "من شأنه أن يلحق ضرراً بالغاً" بالدخول التجاري المتميز الذي تتيحه الولايات المتحدة للإكوادور.[541] رد الرئيس الإكوادوري رفاييل كوريا بالتخلي عن الأرباح التجارة الأمريكية.[542] صرح المتحدث باسم الحكومة أن الإكوادور ستقدم للولايات المتحدة "مساعدة اقتصادية قيمتها 23 مليون دولار سنوياً، تماثل تلك التي تحصل عليها من الأرباح التجارية، بهدف توفير التعليم حول حقوق الإنسان."[543]
انتقد كوريا الإعلام الأمريكي الذي يسلط الضوء على سنودن والبلدان التي تدعمه، بدلاً من التركيز على قضايا الخصوصية العالمية والمحلية التي تناولتها الوثائق المسربة.[544]
بعدما تلقت طائرة الرئيس البوليڤي مورالس، بلاغ كاذب بأن سنودن كان على متنها، أنكر دخوله المجال الجوي الإسپاني، الفرنسي والإيطالي أثناء رحلة العودة من موسكو، انضم رؤساء اوروگواي، الأرجنتين، ڤنزويلا، وسورينام لكوريا وسافر ممثل من البرازيل، إلى كوچاباما، بوليڤيا لمناقشة الحادث.[545] بعد هذا اللقاء، عرض الرئيس نيكولاس مادورو من ڤنزويلا ودانيال اورتگا من نيكاراگوا اللجوء على سنودن.
البرازيل

في سبتمبر 2013، قررت لجنة العلاقات الخارجية في مجلس النواب إرسال ممثل للتحدث مع إدوارد سنودن عن أنشطة تجسس وكالة الأمن القومي في البرازيل.[546] أعلنت پتروناس أنها كانت تستثمر 21 بليون ريال برازيلي على مدار أكثر من خمس سنوات لتحسين أمن بياناتها.[547]
الأمم المتحدة
صرح الأمين العام بان كي مون بأنه "قضية سنودن هي شيء يمكنني اعتباره إهانة" وأن الاتصالات الرقمية يجب ألا "يساء استخدامها كما فعل سنودن".[548]
بيرجيتا يونسدوتير، مشرعة آيسلاندية، انتقدت بان كي كيمون لتعبيره عن وجه نظر شخصية أثناء تحدثه في محفل رسمي. وقالت أن بان "يبدو أنه غير مبالي تماماً بانتهاك الخصوصية من قبل الحكومات حول العالم، ويهتم فقط بكيفية اساءة استخدام منبهو الفساد للنظام."[548]
بلدان أخرى
روسيا، تركيا، وجنوب أفريقيا كان لها رد فعل غاضب بعد ما تبين أنه تم التجسس على دبلوماسيي تلك الدول أثناء قمة العشرين في لندن 2009.[549]
المنبهون للفساد
Daniel Ellsberg, the whistleblower and leaker of the top-secret Pentagon Papers in 1971, stated in an interview with CNN that he thought Snowden had done an "incalculable" service to his country and that his leaks might prevent the United States from becoming a surveillance state. He said Snowden had acted with the same sort of courage and patriotism as a soldier in battle.[550] In an op-ed the following morning, Ellsberg added that "there has not been in American history a more important leak than Edward Snowden's release of NSA material ... including the Pentagon Papers."[551] Ray McGovern, a retired CIA officer turned political activist, agreed with Ellsberg and added, "This time today I'm feeling much more hopeful for our democracy than I was feeling this time yesterday."[552]
William Binney, a whistleblower who disclosed details of the NSA's mass surveillance activities, said that Snowden had "performed a really great public service to begin with by exposing these programs and making the government in a sense publicly accountable for what they're doing." After Snowden cited a conversation with a "reliable source" about allegations that the US was "hacking into China", Binney felt he was "transitioning from whistle-blower to a traitor."[553]
Thomas Drake, former senior executive of NSA and whistleblower, said that he feels "extraordinary kinship" with Snowden. "What he did was a magnificent act of civil disobedience. He's exposing the inner workings of the surveillance state. And it's in the public interest. It truly is."[553][554]
WikiLeaks founder Julian Assange hailed Snowden as a "hero" who has exposed "one of the most serious events of the decade – the creeping formulation of a mass surveillance state."[555] After charges against Snowden were revealed, Assange released a statement asking people to "step forward and stand with" Snowden.[556] Following President Obama's assurances that changes are planned for the NSA surveillance program, Assange said in a written statement that Obama had "validated Edward Snowden's role as a whistle-blower".[557][558]
Shamai Leibowitz, who leaked details about an FBI operation, said that the legal threats and "smear campaign" against Snowden are a "grave mistake" because "If the government really wanted to keep more secrets from coming out, they would do well to let this man of conscience go live his life in some other country."[559]
In October 2013, four US whistleblowers and activists visited Moscow to present Snowden with an award for truth-telling titled The Sam Adams Award for Integrity in Intelligence.[560][561] Thomas Drake, one of the presenters, told reporters after the event that the US had "unchained itself from their own constitution" by banning the "real law and [using] a secret law and secret interpretations of law." He further explained that Snowden "had to escape the US to ensure any chance of freedom", claiming the US had made Snowden stateless by revoking his passport while in Russia, leading to his temporary asylum in the country. Drake praised Russia, saying it had "actually recognized the international law and granted him political asylum".[562]
قائمة الأمريكان تحت المراقبة
في سبتمبر 2013، أفرج للعامة عن أسماء شخصيات بارزة في الولايات المتحدة في أعقاب Interagency Security Classification Appeals Panel-mandated declassification بواسطة الوثائق المرتبطة من وكالة الأمن القومي ورداً على استئناف من أرشيف الأمن القومي في جامعة جورج واشنطن.[565]
الناشطون
- مارتن لوثر كينگ، الابن، زعيم حركة الحريات المدنية للأفارقة الأمريكان، كان تحت رقابة وكالة الأمن القومي حتى يوم اغتياله.[565]
مشاهير
- محمد علي كلاي، بطل الملاكمة السابق في الوزن الثقيل، كان مستهدفاً من قبل مشروع مينارت التابع لوكالة الأمن القومي، حسب وثائق أفرج عنها في سبتمبر 2013.[565]
صحفيون
- أرت بوشوالد ، كاتب عمود في واشنطن پوست، كان مرشحاً من قبل مكتب التحقيقات الفدرالي ليوضح تحت مراقبة وكالة الأمن القومي، حسب وثائق أفرج عنها في سبتمبر 2013.[565]
- توم تويكر، كاتب عامود في نيويورك تايمز، كان من بين قائمة أعداء البيت الأبيض.[565]
أعضاء الكونگرس
- فرنك تشرش، سناتور من إداهو، وضع على قائمة مراقبة وكالة الأمن القومية بسبب آراؤه السياسية "الغير مسؤولة" ونقده لحرب ڤيتنام.[565]
- هاورد بيكر، زعيم أغلبية بمجلس الشيوخ من تنيسي، وضع على قائمة مراقبة مكتب الأمن القومي، حسب وثائق أفرج عنها في سبتمبر 2013.[565]
الإعلام المرتبط بالتسريبات
- Gchq-surveillance-the-documents.pdf
Documents relating to spying on the 2009 G20 Summit
- Upstream-slide.jpg
Upstream and PRISM.
A 2008 Presentation of the XKeyscore program. (PDF, 27.26 MB)
Spying against Enrique Peña Nieto and his associates.
Spying effort against Dilma Rousseff and her advisers.
مقارنة مع التسريبات السابقة
| السنة | الكشف | الحجم | المصدر الرئيسي | الناشرون الكبار |
|---|---|---|---|---|
| 1971 | أوراق الپنتاگون | 4,100 صفحة | دانيال إلسبرگ | النيويورك تايمز |
| 2010 | تسريب البرقيات الدبلوماسية الأمريكية | 251,287 برقية دبلوماسية | تشلسي ماننگ | الگارديان، النيويورك تايمز، در شپيگل، لوموند، إل پايس، ويكيليكس |
| 2013 | الكشف عن التجسس الواسع | 15,000 – 20,000 وثيقة | إدوارد سنودن | الگارديان، النيويورك تايمز، الواشنطن پوست، در شپيگل، لوموند، |
انظر أيضاً
- 2013 Department of Justice investigations of reporters
- Terrorist Finance Tracking Program
- Top Secret America
المصادر
- ^ Greenwald, Glenn. "NSA collecting phone records of millions of Verizon customers daily". The Guardian. Retrieved 16 August 2013.
Exclusive: Top secret court order requiring Verizon to hand over all call data shows scale of domestic surveillance under Obama
- ^ أ ب Fiddler, Stephen (1 July 2013). Echoes of Echelon in Charges of NSA Spying in Europe. The Wall Street Journal.
- ^ Snowden has ‘thousands’ of damaging NSA documents, says Greenwald—MSNBC
- ^ Glenn Greenwald and Ewen MacAskill. "Boundless Informant: the NSA's secret tool to track global surveillance data". The Guardian. Retrieved June 12, 2013.
- ^ "Senators: Limit NSA snooping into US phone records". Associated Press. Retrieved 15 October 2013.
"Is it the goal of the NSA to collect the phone records of all Americans?" Udall asked at Thursday's hearing. "Yes, I believe it is in the nation's best interest to put all the phone records into a lockbox that we could search when the nation needs to do it. Yes," Alexander replied.
- ^ Siobhan Gorman. "Meltdowns Hobble NSA Data Center". The Wall Street Journal. Retrieved 19 October 2013.
The Utah facility, one of the Pentagon's biggest U.S. construction projects, has become a symbol of the spy agency's surveillance prowess, which gained broad attention in the wake of leaks from NSA contractor Edward Snowden.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "USA must not persecute whistleblower Edward Snowden". Amnesty International. Retrieved 16 August 2013.
- ^ "US: Statement on Protection of Whistleblowers in Security Sector". Human Rights Watch. Retrieved 16 August 2013.
- ^ Transparency International Germany. "Transparency International Germany: Whistleblower Prize 2013 for Edward Snowden". Transparency International. Retrieved 16 August 2013.
- ^ "US needs to protect whistleblowers and journalists". Index on Censorship. Retrieved 16 August 2013.
- ^ Snowden Asylum Hits U.S.-Russia Relations - WSJ.com
- ^ U.S. 'Extremely Disappointed' At Russia's Asylum For Snowden : The Two-Way : NPR
- ^ Henderson. "Obama To Leno: 'There Is No Spying On Americans'". NPR. Retrieved 16 August 2013.
- ^ أ ب "New Details Emerge From the Einstein Files; How the F.B.I. Tracked His Phone Calls and His Trash". The New York Times. Retrieved 17 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Cauley, Leslie. "NSA has massive database of Americans' phone calls". "USA Today".
- ^ "Ex-CIA employee source of leak on PRISM program". France 24. Retrieved 17 September 2013.
Snowden's decision to reveal his identity and whereabouts lifts the lid on one of the biggest security leaks in US history and escalates a story that has placed a bright light on Obama's extensive use of secret surveillance.
- ^ "New data show how closely FBI monitored Marilyn Monroe". CBS News. December 28, 2012.
- ^ Ryan Gallagher (2002/05/07). "Documents Show the NSA Spied on Muhammad Ali, Martin Luther King Jr., and … Art Buchwald". Slate (magazine). Retrieved 27 October 2013.
{{cite web}}: Check date values in:|date=(help); Italic or bold markup not allowed in:|publisher=(help) - ^ أ ب U.S. National Security Agency. Early Papers Concerning US-UK Agreement – 1940–1944. Agreement between British Government Code and Cipher School and U.S. War Department dated May 17, 1943. Retrieved: 2013-10-05.
- ^ أ ب ت ث Norton-Taylor, Richard (25 June 2010). "Not so secret: deal at the heart of UK-US intelligence". The Guardian. Retrieved 25 June 2010.
- ^ أ ب ت "Factbox: History of mass surveillance in the United States". Reuters. Retrieved 14 August 2013.
- ^ The Center for Cryptologic History. "The Origins of NSA (NSA.gov)". Web.archive.org. Archived from the original on 18 March 2004.
- ^ Epsley-Jones, Katelyn; Frenzel, Christina. "The Church Committee Hearings & the FISA Court". PBS. Retrieved 14 August 2013.
- ^ "FBI campaign against Einstein revealed". BBC. Retrieved 17 September 2013.
- ^ "Albert Einstein: Fact or Fiction?". History (TV channel). Retrieved 17 September 2013.
Because of his controversial political beliefs-his support for socialism, civil rights, and nuclear disarmament, for example-many anti-Communist crusaders believed that Einstein was a dangerous subversive. Some, like FBI director J. Edgar Hoover, even thought he was a spy. For 22 years, Hoover's agents tapped Einstein's phones, opened his mail, rifled through his trash and even bugged his secretary's nephew's house, all to prove that he was more radical (as his 1,500-page FBI dossier noted) than "even Stalin himself."
- ^ RONALD J. OSTROW and LISA GETTER. "FBI Files on Sinatra Detail Links to JFK, Mob Figures". Los Angeles Times. Retrieved 18 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ MOLOTSKY, IRVIN. "F.B.I. Releases Its Sinatra File, With Tidbits Old and New". The New York Times. Retrieved 18 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "Question: Why is Eleanor Roosevelt's FBI file so large?". George Washington University. Retrieved 18 September 2013.
- ^ "Eleanor Roosevelt". History (TV channel). Retrieved 18 September 2013.
J. Edgar Hoover (1895–1972), the longtime director of the Federal Bureau of Investigation, considered Eleanor Roosevelt's liberal views dangerous and believed she might be involved in communist activities. He ordered his agents to monitor Roosevelt and keep what became an extensive file on her.
- ^ "FBI removes many redactions in Marilyn Monroe file". Associated Press. Retrieved 18 September 2013.
- ^ Cohen, Adam. "While Nixon Campaigned, the F.B.I. Watched John Lennon". The New York Times. Retrieved 18 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "Martin Luther King, Jr. FBI File". Pickler Memorial Library (Truman State University). Retrieved 17 September 2013.
- ^ Church, Frank (April 23, 1976), Church Committee Book III, Church Committee
- ^ "FBI tracked King's every move". CNN. Retrieved 17 September 2013.
- ^ "'Life Lessons' From a White House Plumber". NPR.
When Daniel Ellsberg leaked the Pentagon Papers to The New York Times in 1971, the Nixon White House tried to discredit him. Among other things, Nixon loyalists burglarized the office of Ellsberg's psychiatrist.
- ^ "The Watergate Story". The Washington Post. Retrieved 17 September 2013.
The White House "plumbers" unit - named for their orders to plug leaks in the administration - burglarizes a psychiatrist's office to find files on Daniel Ellsberg, the former defense analyst who leaked the Pentagon Papers.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "Watergate and the Constitution". National Archives and Records Administration. Retrieved 17 September 2013.
- ^ Bamford, James. "The Agency That Could Be Big Brother". The New York Times. Retrieved 14 August 2013.
- ^ DAVID BURNHAM. "TRUMAN WIRETAPS ON EX-NEW DEAL AIDE CITED". The New York Times. Retrieved 18 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "INVESTIGATIONS: Nobody Asked: Is It Moral?". Time. May 10, 1976.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "British intelligence 'birdwatchers spied on Nelson Mandela's hideout'". The Daily Telegraph. Retrieved 21 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "Nelson Mandela 'was spied on by MI6 birdwatchers'". The Times. Retrieved 21 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "NSA Admits to Spying on Princess Diana". The Washington Post. Retrieved 21 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ David Hencke and Rob Evans (6 August 1999). "US holds secret files on Diana". The Guardian.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Campbell, Duncan (12 August 1988). "Somebody's Listening". New Statesman. Archived from the original on 2007-01-03. Retrieved 16 September 2013.
{{cite news}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ أ ب Schmid, Gerhard (11 July 2001). "On the existence of a global system for the interception of private and commercial communications (ECHELON interception system), (2001/2098(INI))" (pdf). European Parliament: Temporary Committee on the ECHELON Interception System. p. 194. Retrieved 16 September 2013.
{{cite web}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ Andrew Bomford (3 November, 1999). "Echelon spy network revealed". BBC.
{{cite web}}: Check date values in:|date=(help) - ^ "UK 'spied on UN's Kofi Annan'". BBC. February, 2004.
{{cite web}}: Check date values in:|year=(help) - ^ James Chapman, Gerri Peev and Ian Drury (30 November 2010). "WikiLeaks are a bunch of terrorists, says leading U.S. congressman as No10 warns of threat to national security". Daily Mail.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "US diplomats spied on UN leadership". The Guardian. Retrieved 27 August 2013.
- ^ "Warrantless Surveillance and the Foreign Intelligence Surveillance Act: The Role of Checks and Balances in Protecting Americans' Privacy Rights (Part II): Hearing Before the H. Comm. on the Judiciary, 110th Cong. 13–30 (statement of J.M. McConnell, Director of National Intelligence)" (PDF). 18 September 2007.
- ^ Risen, James; Lichtblau, Eric. "Bush Lets U.S. Spy on Callers Without Courts". The New York Times. Retrieved 14 August 2013.
The White House asked The New York Times not to publish this article
- ^ "President Visits Troops at Brooke Army Medical Center". White House. 1 January 2006, 12:05 PM CST. Retrieved 15 August 2013.
{{cite web}}: Check date values in:|date=(help) - ^ "AT&T Whistle-Blower's Evidence". Wired. 17 May 2006. Retrieved 14 August 2013.
- ^ Poulsen, Kevin. "Whistle-Blower: Feds Have a Backdoor Into Wireless Carrier — Congress Reacts". Wired. Retrieved 14 August 2013.
- ^ WILLIAM SAFIRE (November 14, 2002). "You Are a Suspect". The New York Times. Retrieved 20 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "WikiLeaks FAQ: What Do the Diplomatic Cables Really Tell Us?". Der Spiegel. Retrieved 14 August 2013.
- ^ Davies, Nick; Leigh, David (25 July 2010). "Afghanistan war logs: Massive leak of secret files exposes truth of occupation". The Guardian. London. Retrieved 26 July 2010.
- ^ "The WikiLeaks Iraq War Logs: Greatest Data Leak in US Military History". Der Spiegel. 22 October 2010. Retrieved 23 October 2010.
- ^ "The NSA Is Building the Country's Biggest Spy Center (Watch What You Say)". Wired. Retrieved 14 August 2013.
- ^ Greenberg, Andy. "NSA Chief Denies Wired's Domestic Spying Story (Fourteen Times) In Congressional Hearing". Forbes. Retrieved 14 August 2013.
- ^ "U.S. agency denies data center to monitor citizens' emails". Reuters. Retrieved 22 September 2013.
- ^ أ ب Laura Poitras, Marcel Rosenbach and Holger Stark. "Codename 'Apalachee': How America Spies on Europe and the UN". Der Spiegel. p. 2. Retrieved 26 August 2013.
- ^ أ ب MacAskill, Ewen; Davies, Nick; Hopkins, Nick; Borger, Julian; Ball, James (17 June 2013). "GCHQ intercepted foreign politicians' communications at G20 summits". The Guardian. London.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ "Edward Snowden: US government has been hacking Hong Kong and China for years". South China Morning Post. Retrieved 9 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Laura Poitras, Marcel Rosenbach, Fidelius Schmid and Holger Stark. "Attacks from America: NSA Spied on European Union Offices". Der Spiegel. Retrieved 9 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: multiple names: authors list (link) - ^ أ ب Staff (31 August 2013). "Snowden Document: NSA Spied On Al Jazeera Communications". Retrieved 31 August 2013.
- ^ ROMERO, SIMON. "N.S.A. Spied on Brazilian Oil Company, Report Says". The New York Times. Retrieved 9 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "US bugged Merkel's phone from 2002 until 2013, report claims". BBC. Retrieved 27 October 2013.
- ^ Duran-Sanchez, Mabel (10 August 2013). "Greenwald Testifies to Brazilian Senate about NSA Espionage Targeting Brazil and Latin America". Retrieved 13 August 2013.
- ^ "Glenn Greenwald afirma que documentos dizem respeito à interesses comerciais do governo americano". 6 August 2013. Retrieved 13 August 2013.
- ^ أ ب How Microsoft handed the NSA access to encrypted messages, The Guardian, 12 July 2013. Retrieved 13 July 2013.
- ^ Bridie Jabour in Sydney (12 July 2013). "Telstra signed deal that would have allowed US spying". The Guardian.
- ^ The first three days of revelations were: the FISC court order that Verizon provide bulk metadata on its customers to the NSA; presentation slides explaining the cooperation of nine US internet giants through the PRISM program; and the bulk collection of Chinese users' text messages, which coincided with Xi Jinping's visit to California to meet Barack Obama.
- ^ أ ب ت ث ج ح Laura Poitras, Marcel Rosenbach and Holger Stark. "Ally and Target: US Intelligence Watches Germany Closely". Der Spiegel. Retrieved 13 August 2013.
- ^ "Colombia asks Kerry to explain NSA spying". The Washington Post. Retrieved 13 August 2013.
- ^ "Greenwald diz que espionagem dá vantagens comerciais e industriais aos Estados Unidos" (in Portuguese). Federal Senate of Brazil. Retrieved 13 August 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ "Greenwald diz que EUA espionam para obter vantagens comerciais" (in Portuguese). Deutsche Welle. Retrieved 13 August 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ "NSA's activity in Latin America is 'collection of data on oil and military purchases from Venezuela, energy and narcotics from Mexico' – Greenwald". Voice of Russia. Retrieved 13 August 2013.
- ^ أ ب "Exclusive: U.S. directs agents to cover up program used to investigate Americans". Reuters. Retrieved 14 August 2013.
- ^ أ ب ت ث ج ح "U.S. spy network's successes, failures and objectives detailed in 'black budget' summary". 29 August 2013. Retrieved 29 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Maass, Peter. "How Laura Poitras Helped Snowden Spill His Secrets". The New York Times. Retrieved 13 August 2013.
- ^ Easley, Jonathan. "Snowden: NSA targeted journalists critical of government after 9/11". The Hill. Retrieved 14 August 2013.
- ^ Laura Poitras, Marcel Rosenbach, Fidelius Schmid and Holger Stark. "Attacks from America: NSA Spied on European Union Offices". Der Spiegel. Retrieved 26 August 2013.
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ "Report: Canada spies targeted Brazil mine ministry". Associated Press. Retrieved 7 October 2013.
- ^ "'Success Story': NSA Targeted French Foreign Ministry". Der Spiegel. Retrieved 24 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ أ ب Shobhan Saxena. "NSA planted bugs at Indian missions in D.C., U.N." The Hindu. Retrieved 24 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Jens Glüsing, Laura Poitras, Marcel Rosenbach and Holger Stark. "Fresh Leak on US Spying: NSA Accessed Mexican President's Email". Der Spiegel. Retrieved 20 October 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: multiple names: authors list (link) - ^ أ ب ت ث Laura Poitras, Marcel Rosenbach, Fidelius Schmid und Holger Stark. "Geheimdokumente: NSA horcht EU-Vertretungen mit Wanzen aus". Der Spiegel (in German). Retrieved 29 June 2013.
{{cite web}}: CS1 maint: multiple names: authors list (link) CS1 maint: unrecognized language (link) - ^ أ ب ت ث ج ح خ د ذ ر "US-Geheimdienst hörte Zentrale der Vereinten Nationen ab". Der Spiegel (in German). Retrieved 25 August 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ أ ب ت ث ج ح "5-nation spy alliance too vital for leaks to harm". Associated Press. Retrieved 29 August 2013.
- ^ أ ب ت "NDB und NSA kooperieren enger als bisher bekannt" (in German). Handelszeitung. Retrieved 18 September 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ أ ب ت unlisted (3 August 2013). "Überwachung: BND leitet massenhaft Metadaten an die NSA weiter". Der Spiegel (in German). Retrieved 3 August 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ أ ب 'Prolific Partner': German Intelligence Used NSA Spy Program, Der Spiegel. Retrieved 21 July 2013.
- ^ "Verfassungsschutz beliefert NSA" (in German). Süddeutsche Zeitung. Retrieved 14 September 2013.
Seit Juli 2013 testet der Verfassungsschutz die Späh- und Analysesoftware XKeyscore. Sollte der Geheimdienst das Programm im Regelbetrieb nutzen, hat sich das BfV verpflichtet, alle Erkenntnisse mit der NSA zu teilen. Das hatte der Präsident des Bundesamtes, Hans-Georg Maaßen, dem US-Dienst zugesichert. Im Januar und Mai war Maaßen zu Besuchen bei der NSA.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: unrecognized language (link) - ^ "Verfassungsschutz beliefert NSA" (in German). Süddeutsche Zeitung. Retrieved 14 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: unrecognized language (link) - ^ أ ب Glenn Greenwald, Laura Poitras and Ewen MacAskill (11 September 2013). "NSA shares raw intelligence including Americans' data with Israel". The Guardian. Retrieved 14 September 2013.
- ^ "NSA asked Japan to tap regionwide fiber-optic cables in 2011". The Japan Times. Retrieved 28 October 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Olmer, Bart. "Ook AIVD bespiedt internetter" (in Dutch). De Telegraaf. Retrieved 10 September 2013.
Niet alleen Amerikaanse inlichtingendiensten monitoren internetters wereldwijd. Ook Nederlandse geheime diensten krijgen informatie uit het omstreden surveillanceprogramma 'Prism'.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: unrecognized language (link) - ^ أ ب ت Dorling, Philip. "Australian spies in global deal to tap undersea cables". The Sydney Morning Herald. Retrieved 29 August 2013.
- ^ أ ب "Sverige deltog i NSA-övervakning" (in Swedish). Svenska Dagbladet. Retrieved 10 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: unrecognized language (link) - ^ Christof Moser and Alan Cassidy. "Geheimdienst-Aufsicht will Kooperation des NDB mit der NSA prüfen" (in German). Schweiz am Sonntag. Retrieved 18 September 2013.
Die NSA hat sowohl mit der Schweiz wie Dänemark eine geheime Vereinbarung abgeschlossen, die den Austausch von Geheimdienstinformationen regelt. Die Vereinbarung berechtigt die NSA, eigene Schlüsselbegriffe in die Abhörsysteme beider Staaten einspeisen zu lassen. Im Tausch für damit gewonnene Erkenntnisse der schweizerischen und dänischen Auslandaufklärung erhalten der NDB und der dänische Geheimdienst PET von der NSA Informationen, die sie im eigenen Land aufgrund gesetzlicher Schranken nicht selber sammeln dürfen. Das geheime Abkommen macht auch die Schweiz zu einem NSA-Horchposten.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ أ ب ت ث ج ح خ د ذ ر ز س ش ص ض ط ظ ع غ ف ق John Goetz, Hans Leyendecker and Frederik Obermaier (28 August 2013). "British Officials Have Far-Reaching Access To Internet And Telephone Communications". Retrieved 28 August 2013.
- ^ "Edward Snowden Interview: The NSA and Its Willing Helpers". Der Spiegel. Retrieved 29 August 2013.
Snowden: Yes, of course. We're (the NSA) in bed together with the Germans the same as with most other Western countries.
- ^ Laura Poitras, Marcel Rosenbach and Holger Stark. "Ally and Target: US Intelligence Watches Germany Closely". Der Spiegel. Retrieved 29 August 2013.
The NSA classifies about 30 other countries as "3rd parties," with whom it cooperates, though with reservations. Germany is one of them. "We can, and often do, target the signals of most 3rd party foreign partners," the secret NSA document reads.
- ^ أ ب ت ث ج Laura Poitras, Marcel Rosenbach and Holger Stark. "iSpy: How the NSA Accesses Smartphone Data". Der Spiegel. Retrieved 9 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Laura Poitras, Marcel Rosenbach, and Holger Stark. "Photo Gallery: Spying on Smartphones". Der Spiegel. Retrieved 9 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: multiple names: authors list (link) - ^ David Leppard and Chris Williams (3 May 2009). "Jacqui Smith's secret plan to carry on snooping". The Sunday Times. Retrieved 3 May 2009.
- ^ Henry Porter. "GCHQ revelations: mastery of the internet will mean mastery of everyone". The Guardian. Retrieved 19 October 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Chris Williams (3 May 2009). "Jacqui's secret plan to 'Master the Internet'". The Register. Retrieved 3 May 2009.
- ^ Chris Williams (3 May 2009). "Jacqui's secret plan to 'Master the Internet'". The Register. Retrieved 3 May 2009.
- ^ أ ب "Agency denies internet spy plans". BBC. Retrieved 19 October 2013.
- ^ Nick Hopkins and Julian Borger. "Exclusive: NSA pays £100m in secret funding for GCHQ". The Guardian. Retrieved 19 October 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Tom Whitehead. "Americans pay GCHQ £100m to spy for them, leaked papers claim". The Daily Telegraph. Retrieved 19 October 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ أ ب "Mueller: FBI uses drones for surveillance over US soil". BBC. Retrieved 24 September 2013.
- ^ Kashmir Hill. "Congress Welcomes The Drones". Forbes. Retrieved 24 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ أ ب rian Bennett and Joel Rubin. "Drones are taking to the skies in the U.S." Los Angeles Times. Retrieved 24 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ MICHAEL KIRKLAND. "Drones over America". United Press International. Retrieved 24 September 2013.
- ^ John D Bates (3 October 2011). "[redacted]" (PDF). p. 16.
- ^ Turner, Shawn (31 July 2013). "DNI Clapper Declassifies and Releases Telephone Metadata Collection Documents". Retrieved 22 August 2013.
- ^ "Minimization Procedures Used by the National Security Agency in Connection with Acquisitions of Foreign Intelligence Information Pursuant to Section 702, as amended" (PDF). 31 October 2011.
- ^ James Ball and Spencer Ackerman (9 August 2013). "NSA loophole allows warrantless search for US citizens' emails and phone calls". Retrieved 12 August 2013.
- ^ أ ب John D Bates (3 October 2011). "[redacted]" (PDF). p. 71.
- ^ أ ب Nakashima, Ellen (21 August 2013). "NSA gathered thousands of Americans' e-mails before court ordered it to revise its tactics". The Washington Post. Retrieved 16 September 2013.
- ^ أ ب "FISA court ruling on illegal NSA e-mail collection program". The Washington Post. 21 August 2013. Retrieved 16 September 2013.
- ^ أ ب Barton Gellman and Matt DeLong (15 August 2013). "First direct evidence of illegal surveillance found by the FISA court". The Washington Post. Retrieved 16 September 2013.
- ^ أ ب Charlie Savage and Scott Shane (21 August 2013). "Secret Court Rebuked N.S.A. on Surveillance". The New York Times. Retrieved 16 September 2013.
- ^ أ ب Mark Hosenball and Tabassum Zakaria (22 August 2013). "NSA collected 56,000 emails by Americans a year: documents". Reuters. NBC News. Retrieved 16 September 2013.
- ^ Perez, Evan (22 August 2013). "NSA misrepresented scope of data collection to secret court". CNN. Retrieved 2 October 2013.
- ^ Turner, Shawn (21 August 2013). "DNI Declassifies Intelligence Community Documents Regarding Collection Under Section 702 of the Foreign Intelligence Surveillance Act (FISA)". Office of the Director of National Intelligence. IC on the Record. Retrieved 2 October 2013.
- ^ Clapper, James (21 August 2013). "DNI James Clapper's Cover Letter Announcing the Document Release" (PDF). Director of National Intelligence. Retrieved 2 October 2013.
- ^ Kimberly Dozier and Stephen Braun (21 August 2013). "NSA Collected Thousands Of Emails, Other Communications By Americans With No Terror Ties". Associated Press. The Huffington Post. Retrieved 2 October 2013.
- ^ Fung, Brian (21 August 2013). "The FISA court got really upset when the NSA didn't tell the truth on surveillance". The Washington Post. Retrieved 16 September 2013.
- ^ Siobhan Gorman and Devlin Barrett (September 10, 2013). "NSA Violated Privacy Protections, Officials Say". Retrieved 10 September 2013.
- ^ Ackerman, Spencer (10 September 2013). "NSA violations led judge to consider viability of surveillance program". The Guardian. Retrieved 16 September 2013.
- ^ Ellen Nakashima, Julie Tate and Carol Leonnig (10 September 2013). "Declassified court documents highlight NSA violations in data collection for surveillance". The Washington Post. Retrieved 14 September 2013.
- ^ Office of the Director of National Intelligence. (10 September). "Declassified FISA court documents on intelligence collection". The Washington Post. Retrieved 14 September 2013.
{{cite news}}: Check date values in:|date=(help) - ^ James R. Clapper (Director of National Intelligence) (10 September 2013). "DNI Clapper Declassifies Intelligence Community Documents Regarding Collection Under Section 501 of the Foreign Intelligence Surveillance Act (FISA)". Office of the Director of National Intelligence. IC On the Record. Retrieved 14 September 2013.
- ^ Tim, Trevor (10 September 2013). "Government Releases NSA Surveillance Docs and Previously Secret FISA Court Opinions In Response to EFF Lawsuit". Electronic Frontier Foundation. Electronic Frontier Foundation. Retrieved 14 September 2013.
- ^ David Kravets. Kim Zetter, Kevin Poulsen (10 September 2013). "NSA Illegally Gorged on U.S. Phone Records for Three Years". Wired.com. Retrieved 22 September 2013.
- ^ Staff (10 August 2013). "US-Geheimdienst: NSA führt Deutschland als Spionageziel".
- ^ Timothy Jones (11 August 2008). "Germany and EU targets for US espionage, Spiegel reports".
- ^ "The Black Budget". 29 August 2013. Retrieved 29 August 2013.
- ^ "NSA shares raw intelligence including Americans' data with Israel". September 11, 2013. Retrieved 11 September 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Sailor IV, F. Dennis (13 September 2013). "United States Foreign Intelligence Surveillance Court In Re Orders of this Court Interpretating Section 215 of the Patriot Act (Docket No. Misc. 13-02)" (PDF). www.uscourts.gov. Retrieved 15 September 2013.
- ^ Fung, Brian (13 September 2013). "The FISA court will release more opinions because of Snowden". The Washington Post. Retrieved 15 September 2013.
- ^ Ackerman, Spencer (13 September 2013). "Fisa judge: Snowden's NSA disclosures triggered important spying debate". The Guardian. Retrieved 16 September 2013.
- ^ أ ب "Ally and Target: US Intelligence Watches Germany Closely". 12 August 2013. Retrieved 12 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Gellman, Barton (16 August 2013). "NSA broke privacy rules thousands of times per year, audit finds". Retrieved 16 August 2013.
- ^ "U.S. documents detail al-Qaeda's efforts to fight back against drones". 3 September 2013. Retrieved 3 September 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ "Top-secret U.S. intelligence files show new levels of distrust of Pakistan". 2 September 2013. Retrieved 3 September 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Staff (4 September 2013). "US intelligence uncovered Pak army plot to kill Asma Jahangir in India: report". Retrieved 4 September 2013.
- ^ Staff (September 7, 2013). "Privacy Scandal: NSA Can Spy on Smart Phone Data". Retrieved 7 September 2013.
- ^ A published heat map shows that most data is collected from Iran, Pakistan and Jordan, with over 40 billion individual pieces of information collected from these three countries alone in March 2013 alone, from a total of 97 billion worldwide.
- ^ أ ب ت ث ج ح خ د ذ ر ز س ش ص ض ط ظ ع "NSA report on privacy violations in the first quarter of 2012". The Washington Post. 16 August 2013. Retrieved 16 August 2013.
- ^ Snowden reveals Australia's links to US spy web, The Sydney Morning Herald, 8 July 2013. Retrieved 11 July 2013.
- ^ أ ب ت ث ج Glenn Greenwald and Spencer Ackerman (27 June 2013). "How the NSA is still harvesting your online data". The Guardian. Retrieved 1 August 2013.
- ^ أ ب ت "What to say, and not to say, to 'our overseers'". 16 August 2013. Retrieved 16 August 2013.
- ^ أ ب ت ث Staff (29 July 2013). "Photo Gallery: NSA Documentation of Spying in Germany". Retrieved 11 August 2013.
- ^ أ ب Barton Gellman and Matt DeLong (15 August 2013). "What to say, and not to say, to 'our overseers'". The Washington Post. Retrieved 25 August 2013.
- ^ أ ب ت ث ج ح "Codename 'Apalachee': How America Spies on Europe and the UN". 26 August 2013. Retrieved 26 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ أ ب ت ث ج James Ball, Julian Borger and Glenn Greenwald (2013-09-05). "US and UK spy agencies defeat privacy and security on the internet". The Guardian. Retrieved 2013-09-05.
- ^ "Project Bullrun – classification guide to the NSA's decryption program". September 5, 2013.
- ^ أ ب Barton Gellman and Matt DeLong (15 August 2013). "First direct evidence of illegal surveillance found by the FISA court". The Washington Post. Retrieved 25 August 2013.
- ^ أ ب ت ث ج ح خ NSA slides explain the PRISM data-collection program, The Washington Post, 6 June 2013, updated 10 July 2013. Retrieved 12 July 2013.
- ^ أ ب ت ث Siobhan Gorman and Jennifer Valentiono-Devries (20 August 2013). "New Details Show Broader NSA Surveillance Reach – Programs Cover 75% of Nation's Traffic, Can Snare Emails". The Wall Street Journal. Retrieved 21 August 2013.
- ^ أ ب "New slides about NSA collection programs". Top Level Telecommunications. 16 July 2013 and updated on July 16, 2013. Retrieved 27 August 2013.
{{cite web}}: Check date values in:|date=(help) - ^ Kloc, Joe (12 July 2013). "Forget PRISM: FAIRVIEW is the NSA's project to "own the Internet"". Retrieved 11 August 2013.
- ^ "Espionagem dos EUA se espalhou pela América Latina". 12 July 2013. Retrieved 11 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ أ ب ت "The National Security Agency: Missions, Authorities, Oversight and Partnerships" (PDF). National Security Agency. 9 August 2013. Retrieved 12 August 2013.
- ^ أ ب ت Perez, Evan (10 August 2013). "Documents shed light on U.S. surveillance programs". CNN. Retrieved 12 August 2013.
- ^ أ ب Craig Timberg and Barton Gellman (30 August 2013). "NSA paying U.S. companies for access to communications networks". The Washington Post. Retrieved 31 August 2013.
- ^ أ ب "NSA loophole allows warrantless search for US citizens' emails and phone calls". 9 August 2013. Retrieved 11 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ أ ب ت Nakashima, Ellen (31 July 2013). "Newly declassified documents on phone records program released". The Washington Post. Retrieved 4 August 2013.
- ^ أ ب ت ث ج Ambinder, Marc (14 August 2013). "An Educated Guess About How the NSA Is Structured". Retrieved 14 August 2013.
- ^ أ ب Gellman, Barton (15 June 2013). "U.S. surveillance architecture includes collection of revealing Internet, phone metadata". Retrieved 11 August 2013.
- ^ أ ب Staff (September 15, 2013). "'Follow the Money': NSA Spies on International Payments 'Follow the Money': NSA Spies on International Payments". Retrieved 15 September 2013.
- ^ أ ب ت ث Staff (1 September 2013). "'Success Story': NSA Targeted French Foreign Ministry". Retrieved 1 September 2013.
- ^ أ ب "Jornal O Globo revela que Brasil teria sido espionado pelos Estados Unidos". 8 July 2013. Retrieved 5 September 2013.
- ^ أ ب Peterson, Josh (27 June 2013). "Report: NSA Internet spying program collected half-a-trillion records in 2012". The Daily Caller. Retrieved 29 July 2013.
- ^ أ ب Bamford, James (12 July 2013). "They Know Much More Than You Think". The New York Review of Books. Retrieved 29 July 2013.
- ^ No alvo dos EUA, Infographic, O Globo. Retrieved 8 July 2013.
- ^ James Ball, Julian Borger and Glenn Greenwald (6 September 2013). "Revealed: how US and UK spy agencies defeat internet privacy and security". The Guardian. Retrieved 7 September 2013.
- ^ أ ب Ball, James (25 October 2013). "Leaked memos reveal GCHQ efforts to keep mass surveillance secret". The Guardian. Retrieved 25 October 2013.
- ^ أ ب "Exclusive: Edward Snowden leaks reveal UK's secret Middle-East web surveillance base". 22 August 2013. Retrieved 22 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Greenwald, Glenn (23 August 2013). "Snowden: UK government now leaking documents about itself". Retrieved 23 August 2013.
- ^ staff (September 16, 2013). "'Foreign nation with significant means' in spying on Belgium probe". Retrieved September 16, 2013.
- ^ Schmitz, Gregor-Peter (September 20, 2013). "Cyber Attack: Belgians Angered by British Spying". Retrieved September 20, 2013.
- ^ Gallagher, Ryan (September 20, 2013). "http://www.slate.com/blogs/future_tense/2013/09/20/operation_socialist_u_k_s_gchq_hacked_belgacom_snowden_documents_reveal.html". Retrieved September 20, 2013.
{{cite news}}: External link in|title= - ^ أ ب Goebel, Nicole (25 August 2013). Schuster, Kathleen (ed.). "NSA spied on UN, German report says". Deutsche Welle. Retrieved 25 August 2013.
- ^ "NSA bugged UN headquarters – newspaper". 25 August 2013. Retrieved 25 August 2013.
- ^ "To hunt Osama bin Laden, satellites watched over Abbottabad, Pakistan, and Navy SEALs". 29 August 2013. Retrieved 29 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Brooks, Bradley (1 September 2013). "Report: NSA spied on leaders of Brazil, Mexico". Retrieved 1 September 2013.
- ^ "Saiba como o maior sistema de espionagem do mundo monitora comunicações em Brasília". 1 September 2013. Retrieved 1 September 2013.
{{cite news}}: Unknown parameter|editors=ignored (|editor=suggested) (help) - ^ "EUA espionaram Dilma". 1 September 2013. Retrieved 1 September 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Barton Gellman and Ashkan Soltani (2013-10-14). "NSA collects millions of e-mail address books globally".
- ^ أ ب "NSA surveillance: A guide to staying secure". The Guardian. Retrieved 24 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ أ ب ت Narayan Lakshman. "Secret bunkers, a challenge for U.S. intelligence". The Hindu. Retrieved 24 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Nelson, Kimberly (22 August 2013). "In Salt Lake for the 2002 Olympics? Your texts, emails and phone calls likely reviewed by NSA". Retrieved 25 August 2023.
- ^ Davidson, Lee (23 August 2013). "Former Salt Lake mayor: NSA snooping is the scandal of the century". Retrieved 25 August 2013.
- ^ Freeze, Colin (15 June 2013). "How Canada's shadowy metadata-gathering program went awry". Retrieved 27 August 2013.
- ^ "Raw documents: Canada's 'top secret' data mining program". 10 June 2013. Retrieved 27 August 2013.
- ^ Freeze, Colin (10 June 2013). "Data-collection program got green light from MacKay in 2011". Retrieved 27 August 2013.
- ^ "The NYPD Division of Un-American Activities". 25 August 2013. Retrieved 26 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ "Blue Coat". Reporters Without Borders. 12 March 2013.
- ^ Citizen Lab, Munk School of Global Affairs, University of Toronto (15 January 2013). "Planet Blue Coat: Mapping Global Censorship and Surveillance Tools".
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ Markoff, John (16 January 2013). "Rights Group Reports on Abuses of Surveillance and Censorship Technology". The New York Times.
- ^ Nakashima, Ellen (8 July 2013). "Web monitoring devices made by U.S. firm Blue Coat detected in Iran, Sudan". The Washington Post.
- ^ "You Are Being Tracked: How License Plate Readers Are Being Used to Record Americans' Movements". 17 July 2013. Retrieved 11 August 2013.
- ^ Martinez, Michael (18 July 2013). "ACLU raises privacy concerns about police technology tracking drivers". Retrieved 11 August 2013.
- ^ McCullagh, Declan (2 August 2013). "FBI pressures Internet providers to install surveillance software".
- ^ "FBI Taps Hacker Tactics to Spy on Suspects". 3 August 2013. Retrieved 12 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Choney, Suzanne (6 August 2013). "FBI hacking squad used in domestic investigations, experts say". Retrieved 12 August 2013.
- ^ Savage, Charlie (8 August 2013). "N.S.A. Said to Search Content of Messages to and From U.S". Retrieved 11 August 2013.
- ^ Nixon, Ron (3 July 2013). "U.S. Postal Service Logging All Mail for Law Enforcement". Retrieved 11 August 2013.
{{cite news}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ Dharmakumar, Rohin (13 August 2013). "Keep your virtual life away from prying governments". Retrieved 13 August 2013.
- ^ Parbat, Kalyan (27 July 2013). "Israel's Verint to get government contract for interception tools". Retrieved 13 August 2013.
- ^ Kirka, Danica (19 August 2013). "Partner of reporter at center of NSA leak detained". Retrieved 19 August 2013.
- ^ Staff (21 August 2013). "New Zealand passes bill allowing domestic spying". Retrieved 23 August 2013.
- ^ Watkins, Tracy (21 August 2013). "Spy bill passes into law amid wide criticism". Retrieved 23 August 2013.
- ^ "Podcast Show #112: NSA Whistleblower Goes on Record -Reveals New Information & Names Culprits!" (Podcast). 19 June 2013. Retrieved 15 August 2013.
- ^ Hill, Kashmir (24 July 2013). "Blueprints of NSA's Ridiculously Expensive Data Center in Utah Suggest It Holds Less Info Than Thought". Retrieved 11 August 2013.
- ^ أ ب Priest, Dana (21 July 2013). "NSA growth fueled by need to target terrorists". Retrieved 11 August 2013.
- ^ "Exclusive: U.S. directs agents to cover up program used to investigate Americans". 5 August 2013. Retrieved 11 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ "Exclusive: IRS manual detailed DEA's use of hidden intel evidence". 7 August 2013. Retrieved 12 August 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Lindsay, Jonathan S (27 July 2013). "U.S. allowed Italian kidnap prosecution to shield higher-ups, ex-CIA officer says". Retrieved 11 August 2013.
- ^ Obama’s crackdown views leaks as aiding enemies of U.S., McClatchy, 20 June 2013. Retrieved 12 July 2013.
- ^ "Stellungnahme des BSI zur aktuellen Berichterstattung zu MS Windows 8 und TPM". 21 August 2013. Retrieved 22 August 2013.
- ^ Staff (22 August 2013). "German Federal Government Warns on the Security Dangers of Windows 8". Retrieved 22 August 2013.
- ^ "U.S. intelligence agencies spend millions to hunt for insider threats, document shows". 1 September 2013. Retrieved 2 September 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help) - ^ Strohm, Chris (23 August 2013). "Lawmakers Probing Intentional Abuses of Power by NSA Analysts". Retrieved 23 August 2013.
- ^ Gorman, Siobhan (23 August 2013). "NSA Officers Sometimes Spy on Love Interests". Retrieved 23 August 2013.
- ^ "Drug Agents Use Vast Phone Trove, Eclipsing N.S.A.'s". 1 August 2013,. Retrieved 2 August 2013.
{{cite news}}: Check date values in:|date=(help); Cite uses deprecated parameter|authors=(help)CS1 maint: extra punctuation (link) - ^ "Synopsis of the Hemisphere Project". 1 September 2013. Retrieved 2 September 2013.
- ^ Andersson, Aron (September 6, 2013). "Video: Här pekar Duncan Campbell ut Sverige" (in Swedish). Retrieved 7 September 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ "Uppgifter om Sverige fick inte publiceras" (in Swedish). September 6, 2013. Retrieved 7 September 2013.
{{cite news}}: Cite uses deprecated parameter|authors=(help)CS1 maint: unrecognized language (link) - ^ Staff (September 6, 2013). "Sweden sits on pipeline of intelligence 'gold'". Retrieved 7 September 2013.
- ^ Staff (September 8, 2013). "Datenbank PX: CIA und deutsche Dienste betrieben jahrelang Geheimprojekt" (in German). Retrieved 8 September 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ Greenberg, Andy (September 17, 2013). "Amid NSA Scandal, ACLU Report Turns Spotlight Back To FBI's 'Unchecked Abuse Of Authority'". Retrieved September 17, 2013.
- ^ "Unleashed and Unaccountable: The FBI's Unchecked Abuse of Authority". September 17, 2013. Retrieved September 17, 2013.
- ^ Cushing, Tim (September 18, 2013). "NSA Apparently Purchasing Software Exploits From French Security Firm". Retrieved September 18, 2013.
- ^ أ ب "How Edward Snowden led journalist and film-maker to reveal NSA secrets". The Guardian. Retrieved 20 August 2013.
- ^ أ ب Mark Hosenball (15 August 2013), Snowden downloaded NSA secrets while working for Dell, sources say Reuters
- ^ أ ب Peter Maass (18 August 2013), How Laura Poitras Helped Snowden Spill His Secrets The New York Times
- ^ Carmon, Irin (10 June 2013). "How we broke the NSA story". Salon. Retrieved 11 June 2013.
- ^ Greenwald, Glenn; MacAskill, Ewen; Poitras, Laura (9 June 2013). "Edward Snowden: the whistleblower behind the NSA surveillance revelations". The Guardian. London. Retrieved 9 June 2013.
- ^ Smith, Matt; Pearson, Michael (10 June 2013). "NSA leaker holed up in Hong Kong hotel, running low on cash". CNN. Retrieved 10 June 2013.
- ^ "U.S., British intelligence mining data from nine U.S. Internet companies in broad secret program". The Washington Post. Retrieved 20 August 2013.
- ^ أ ب Ball, James (24 October 2013). "NSA monitored calls of 35 world leaders after US official handed over contacts". The Guardian. Retrieved 24 October 2013.
- ^ Gellman, Barton; Poitras, Laura (6 June 2013). "US Intelligence Mining Data from Nine U.S. Internet Companies in Broad Secret Program". The Washington Post. Retrieved 15 June 2013.
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ Greenwald, Glenn; MacAskill, Ewen (6 June 2013). "NSA Prism program taps in to user data of Apple, Google and others". The Guardian. Retrieved 15 June 2013.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ Glenn Greenwald (6 June 2013). "NSA collecting phone records of millions of Verizon customers daily". The Guardian. Retrieved 16 September 2013.
{{cite news}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ MacAskill, Ewen; Borger, Julian; Hopkins, Nick; Davies, Nick; Ball, James (21 June 2013). "GCHQ taps fiber-optic cables for secret access to world's communications". The Guardian.
- ^ Glenn Greenwald and Spencer Ackerman (27 June 2013). "NSA collected US email records in bulk for more than two years under Obama". The Guardian. Retrieved 1 August 2013.
- ^ MacAskill, Ewen; Borger, Julian (30 June 2013). "New NSA leaks show how US is bugging its European allies". The Guardian. London.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ Glenn Greenwald, Ewen MacAskill, Laura Poitras, Spencer Ackerman and Dominic Rushe (11 July 2013). "Revealed: how Microsoft handed the NSA access to encrypted messages". The Guardian. Retrieved 11 July 2013.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ Greenwald, Glenn (31 July 2013)."XKeyscore: NSA tool collects 'nearly everything a user does on the internet' – XKeyscore Gives 'Widest-Reaching' Collection of Online Data – NSA Analysts Require No Prior Authorization for Searches – Sweeps Up Emails, Social Media Activity and Browsing History". The Guardian. Retrieved 1 August 2013.
- ^ Charlie Savage and David E. Sanger (31 July 2013). "Senate Panel Presses N.S.A. on Phone Logs". The New York Times. Retrieved 4 August 2013.
- ^ James Ball, Luke Harding and Juliette Garside (1 August 2013). "Exclusive: NSA pays £100m in secret funding for GCHQ". Retrieved 2 August 2013.
- ^ James Ball and Spencer Ackerman (9 August 2013). "NSA loophole allows warrantless search for US citizens' emails and phone calls – Exclusive: Spy agency has secret backdoor permission to search databases for individual Americans' communications". The Guardian. Retrieved 12 August 2013.
- ^ Farivar, Cyrus (10 August 2013). "New leak: NSA can search US e-mail data but theoretically won't". Ars Technica. Retrieved 13 August 2013.
- ^ Ball, James (21 August 2013). "Edward Snowden NSA files: secret surveillance and our revelations so far – Leaked National Security Agency documents have led to several hundred Guardian stories on electronic privacy and the state". The Guardian. Retrieved 24 August 2013.
- ^ Roberts, Dan (23 August 2013). "US surveillance guidelines not updated for 30 years, privacy board finds – Privacy watchdog points out in letter to intelligence chiefs that rules designed to protect Americans are severely outdated". The Guardian. Retrieved 24 August 2013.
- ^ Medine, David (22 August 2013). "2013-08-22 Privacy and Civil Liberties Oversight Board letter to US Attorney General Eric Holder and Directer of National Intelligence James Clapper" (PDF). amazonnews.com. Retrieved 24 August 2013.
- ^ MacAskill, Ewen (23 August 2013). "NSA paid millions to cover Prism compliance costs for tech companies • Top-secret files show first evidence of financial relationship • Prism companies include Google and Yahoo, says NSA • Costs were incurred after 2011 Fisa court ruling". The Guardian. Retrieved 24 August 2013.
- ^ "NSA and Israeli intelligence: memorandum of understanding – full document". The Guardian. 11 September 2013. Retrieved 14 September 2013.
- ^ Barton Gellman and Laura Poitras (6 June 2013). "U.S., British intelligence mining data from nine U.S. Internet companies in broad secret program". The Washington Post. Retrieved 24 August 2013.
- ^ Gellmann, Barton (16 August 2013). "NSA broke privacy rules thousands of times per year, audit finds". The Washington Post. Retrieved 24 August 2013.
- ^ Nakashima, Ellen (16 August 2013). "Lawmakers, privacy advocates call for reforms at NSA". The Washington Post. Retrieved 25 August 2013.
- ^ Gellmann, Barton (16 August 2013). "NSA statements to The Post". The Washington Post. Retrieved 25 August 2013.
- ^ Barton Gellman and Matt DeLong (15 August 2013). "What's a 'violation'?". The Washington Post. Retrieved 25 August 2013.
- ^ Leonnig, Carol D. (16 August 2013). "Court: Ability to police U.S. spying program limited". The Washington Post. Retrieved 25 August 2013.
- ^ Wallsten, Peter (17 August 2013). "House panel withheld document on NSA surveillance program from members". The Washington Post. Retrieved 25 August 2013.
- ^ Weich, Ronald. "Report of the National Security Agency's Bulk Collection Programs for USA PATRIOT Act Reauthorization" (PDF). Office of the Assistant Attorney General. Director of National Intelligence. Retrieved 25 August 2013.
- ^ Aid, Matthew M. (10 June 2013). "Inside the NSA's Ultra-Secret China Hacking Group". Foreign Policy. Retrieved 11 June 2013.
- ^ Barton Gellman. "Secret documents detail U.S. war in cyberspace". The Washington Post (via The Japan Times). Retrieved 2 September 2013.
- ^ Barton Gellman and Ellen Nakashima (31 August 2013). "U.S. spy agencies mounted 231 offensive cyber-operations in 2011, documents show". The Washington Post. Retrieved 31 August 2013.
- ^ Konrad Lischka und Julia Stanek (31 August 2013). "Cyber-Angriffe: USA infizieren Zehntausende Computer mit NSA-Trojanern". Der SPIEGEL (in German). Retrieved 31 August 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ Zetter, Kim (4 September 2013). "NSA Laughs at PCs, Prefers Hacking Routers and Switches". Wired.com. Retrieved 2 October 2013.
- ^ Nakashima, Ellen (2 October 2013). "NSA had test project to collect data on Americans' cellphone locations, director says". The Washington Post. Retrieved 18 October 2013.
- ^ Ehrenfreud, Max (15 October 2013). "Leaks by Edward Snowden suggest NSA collects millions of Americans' address books". The Washington Post. Retrieved 18 October 2013.
- ^ Barton Gellman and Ashkan Soltani (15 October 2013). "NSA collects millions of e-mail address books globally". The Washington Post. Retrieved 18 October 2013.
- ^ Barton Gellman and Matt DeLong (15 October 2013). "The NSA's problem? Too much data". The Washington Post. Retrieved 18 October 2013.
- ^ Barton Gellman and Matt DeLong (15 October 2013). "SCISSORS: How the NSA collects less data". The Washington Post. Retrieved 18 October 2013.
- ^ Barton Gellman and Matt DeLong (15 October 2013). "An excerpt from the NSA's Wikipedia". The Washington Post. Retrieved 18 October 2013.
- ^ Soltani, Ashkan (14 October 2013). "Here's everything you should know about NSA address book spying in one FAQ". The Washington Post. Retrieved 18 October 2013.
- ^ Jennifer Valentino-Devries and Danny Yadron (1 August 2013). "FBI Taps Hacker Tactics to Spy on Suspects". The Wall Street Journal. Retrieved 9 October 2013.
- ^ Jennifer Valentino-DeVries and Danny Yadron (1 August 2013). "How the FBI Hacks Criminal Suspects". The Wall Street Journal. Retrieved 9 October 2013.
- ^ "Graphic: How the NSA Scours Internet Traffic in the U.S." The Wall Street Journal. 20 August 2013. Retrieved 21 August 2013.
- ^ Jennifer Valentiono-Devries and Siobhan Gorman (20 August 2013). "What You Need to Know on New Details of NSA Spying". The Wall Street Journal. Retrieved 21 August 2013.
- ^ Angwin, Julia (13 December 2012). "U.S. Terrorism Agency to Tap a Vast Database of Citizens". The Wall Street Journal. Retrieved 21 August 2013.
- ^ Savage, Charlie (8 August 2013). "N.S.A. Said to Search Content of Messages to and From U.S." The New York Times. Retrieved 30 September 2013.
- ^ James Risen and Laura Poitras (28 September 2013). "N.S.A. Gathers Data on Social Connections of U.S. Citizens". The New York Times. Retrieved 30 September 2013.
- ^ Strohm, Chris (24 August 2013). "Lawmakers Probe Willful Abuses of Power by NSA Analysts". Bloomberg News. Retrieved 24 August 2013.
- ^ Roberts, Dan (23 August 2013). "NSA analysts deliberately broke rules to spy on Americans, agency reveals – Inspector general's admission undermines fresh insistences from president that breaches of privacy rules were inadvertent". The Guardian. Retrieved 24 August 2013.
- ^ Gorman, Siobhan (23 August 2013). "NSA Officers Spy on Love Interests". The Wall Street Journal. Retrieved 24 August 2013.
- ^ EXCLUSIVE: US hacks Chinese mobile phone companies, South China Morning Post
- ^ NSA targeted China's Tsinghua University in hacking attacks, South China Morning Post
- ^ Lam, Lana (23 June 2013). "US hacked Pacnet, Asia Pacific fibre-optic network operator, in 2009". South China Morning Post (Hong Kong). Retrieved 25 June 2013.
- ^ Laura Poitras, Marcel Rosenbach und Holger Stark. "Geheimdokumente: NSA überwacht 500 Millionen Verbindungen in Deutschland". Der Spiegel (in German). Retrieved 30 June 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ Iain Thomson (8 July 2013). "Snowden: US and Israel did create Stuxnet attack code". The Register. Retrieved 8 July 2013.
- ^ "Interview mit Edward Snowden: NSA liefert BND Werkzeuge für Lauschangriff". Der Spiegel (in German). 7 July 2013. Retrieved 14 September 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ "Snowden: NSA steckte "unter einer Decke mit den Deutschen" Zusammenarbeit zwischen US-Geheimdienst und BND offenbar enger als bekannt" (in German). Deutschlandradio. 7 July 2013. Retrieved 14 September 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ unlisted (3 August 2013). "Überwachung: BND leitet massenhaft Metadaten an die NSA weiter". Retrieved 3 August 2013.
- ^ Geiger, Friedrich (3 August 2013). "German Intelligence Agency Providing NSA With Metadata – Report". Retrieved 3 August 2013.
- ^ Mass Data: Transfers from Germany Aid US Surveillance 5 August 2013
- ^ "Snowden-Enthüllungen: NSA spionierte al-Dschasira aus". Der SPIEGEL (in German). 31 August 2013. Retrieved 31 August 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ "'Follow the Money': NSA Spies on International Payments". Der Spiegel. 15 September 2013. Retrieved 24 September 2013.
- ^ Jens Glüsing, Laura Poitras, Marcel Rosenbach and Holger Stark (20 October 2013). "Fresh Leak on US Spying: NSA Accessed Mexican President's Email". Der Spiegel. Retrieved 22 October 2013.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ "NSA-Spionage: Mexiko fordert Aufklärung über US-Bespitzelungen". Der Spiegel (in German). 21 October 2013. Retrieved 22 October 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ Jacob Appelbaum, Holger Stark, Marcel Rosenbach and Jörg Schindler (23 October 2013). "Berlin Complains: Did US Tap Chancellor Merkel's Mobile Phone?". Der Spiegel. Retrieved 25 October 2013.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ Fischer, Sebastian (24 October 2013). "Merkel's Phone: Spying Suspicions Put Obama in a Tight Spot". Der Spiegel. Retrieved 25 October 2013.
- ^ Charly Wilder and Rupert Neat (24 October). "'Out of Hand': Europe Furious Over US Spying Allegations". Der Spiegel. Retrieved 25 October 2013.
{{cite news}}: Check date values in:|date=(help) - ^ Ian Traynor in Brussels, Philip Oltermann in Berlin, and Paul Lewis in Washington (24 October). "Angela Merkel's call to Obama: are you bugging my mobile phone?". The Guardian. Retrieved 25 October 2013.
{{cite news}}: Check date values in:|date=(help)CS1 maint: multiple names: authors list (link) - ^ Ball, James (25 October 2013). "NSA monitored calls of 35 world leaders after US official handed over contacts". The Guardian. Retrieved 25 October 2013.
- ^ Traynor, Ian (25 October 2013). "Germany and France warn NSA spying fallout jeopardises fight against terror". The Guardian. Retrieved 25 October 2013.
- ^ "NSA-Überwachung: Merkels Handy steht seit 2002 auf US-Abhörliste". Der Spiegel (in German). 26 October 2012. Retrieved 26 October 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ "U.S. monitored German Chancellor Angela Merkel's phone since 2002". Reuters. The Daily Mail. 26 October 2012. Retrieved 26 October 2013.
- ^ Ofer Aderet (26 October 2015). "Obama: Had I known NSA tapped Merkel's cell, I would have stopped it, German media reports". Haaretz. Retrieved 26 October 2013.
- ^ David E. Sanger and Mark Mazzetti (24 October 2013). "Allegation of U.S. Spying on Merkel Puts Obama at Crossroads". The New York Times. Retrieved 26 October 2013.
- ^ EUA espionaram milhões de e-mails e ligações de brasileiros, O Globo, 6 July 2013. Retrieved 8 July 2013.
- ^ The NSA's mass and indiscriminate spying on Brazilians, Glenn Greenwald, The Guardian, 7 July 2013. Retrieved 8 July 2013.
- ^ EUA expandem o aparato de vigilância continuamente, O Globo, 6 July 2013. Retrieved 8 July 2013.
- ^ Philip Dorling (8 July 2013). "Snowden reveals Australia's links to US spy web". The Age World. Retrieved 8 July 2013.
- ^ أ ب "Brazil Angered Over Report N.S.A. Spied on President". The New York Times. Retrieved 16 September 2013.
{{cite news}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ "NSA Documents Show United States Spied Brazilian Oil Giant". Jornal da Globo Fantástico. 8 September 2013. Retrieved 24 September 2013.
- ^ "Ministério de Minas e Energia está na mira de espiões americanos e canadenses". O Globo. 6 October 2013. Retrieved 8 October 2013.
- ^ "Report: Canada spies targeted Brazil mine ministry". The Associated Press. The Associated Press. 6 October 2013. Retrieved 8 October 2013.
- ^ Ockenden, Will (8 October 2013). "Australia prepared briefing on US global internet spying program PRISM before Snowden revelations". ABC News (Australia). Retrieved 8 October 2013.
- ^ "AG Department Prism FOI PDF". ABC News Online. 27 June 2013. Retrieved 8 October 2013.
- ^ "NDR/SZ: Neue Dokumente belasten britischen Geheimdienst – Deutsche Telekom verlangt Auskünfte". NDR Presse und Information (in German). NDR. 28 August 2013. Retrieved 30 August 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ أ ب John Goetz, Hans Leyendecker and Frederik Obermaier (28 August 2013). "Britischer Geheimdienst zapft Daten aus Deutschland ab". Süddeutsche Zeitung (in German). Retrieved 30 August 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ أ ب ت ث ج ح خ د John Goetz and Frederik Obermaier. "Snowden enthüllt Namen der spähenden Telekomfirmen". Süddeutsche Zeitung (in German). Retrieved 2 August 2013.
In den internen Papieren des GCHQ aus dem Jahr 2009 stehen sie nun aufgelistet: Verizon Business, Codename: Dacron, British Telecommunications (codenamed "Remedy"), Vodafone Cable ("Gerontic"), Global Crossing ("Pinnage"), Level 3 (codenamed "Little"), Viatel ("Vitreous") und Interoute ("Streetcar").
{{cite web}}: CS1 maint: unrecognized language (link) - ^ "Snowden enthüllt Namen der spähenden Telekomfirmen". Süddeutsche Zeitung. Retrieved 2 August 2013.
- ^ "Verfassungsschutz spionierte für Geheimdienste - Bundesamt-Chef Maaßen stimmte zu". Norddeutscher Rundfunk (in German). Norddeutscher Rundfunk. 13 September 2013. Retrieved 14 September 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ "Verfassungsschutz beliefert NSA". Süddeutsche Zeitung (in German). 13 September 2013. Retrieved 14 September 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ "Auch Verfassungsschutz liefert Daten an NSA "Süddeutsche Zeitung" und NDR berichten über intensiven Datenaustausch". Deutschland Radio (in German). Deutschland Radio. 13 September 2013. Retrieved 14 September 2013.
{{cite web}}: CS1 maint: unrecognized language (link) - ^ "Frankreich liefert Informationen an britische und US-Geheimdienste". Süddeutsche Zeitung (in German). 26 October 2013. Retrieved 26 October 2013.
{{cite news}}: CS1 maint: unrecognized language (link) - ^ Nicole Perlroth, Jeff Larson and Scott Shane (2013-09-05). "N.S.A. Foils Much Internet Encryption". The New York Times. Retrieved 2013-09-05.
- ^ "Secret Documents Reveal N.S.A. Campaign Against Encryption". The New York Times. 5 September 2013. Retrieved 7 September 2013.
- ^ "Unlocking Private Communications". The New York Times. 5 September 2013. Retrieved 7 September 2013.
- ^ Perlroth, Nicole, Larson, Jeff, and Shane, Scott (September 5, 2013). "The NSA's Secret Campaign to Crack, Undermine Internet Security". ProPublica.
{{cite news}}: Italic or bold markup not allowed in:|publisher=(help)CS1 maint: multiple names: authors list (link) - ^ Nakashima, Ellen (6 September 2013). "NSA has made strides in thwarting encryption used to protect Internet communication". The Washington Post. Retrieved 7 September 2013.
- ^ Jacques Follorou and Glenn Greenwald (21 October 2013). "France in the NSA's crosshair : phone networks under surveillance". Le Monde. Retrieved 22 October 2013.
- ^ Gearan, Anna (22 October 2013). "Report that NSA collected French phone records causing diplomatic headache for U.S." The Washington Post. Retrieved 22 October 2013.
- ^ "Espionnage de la NSA : tous les documents publiés par "Le Monde"". Le Monde. 21 October 2013. Retrieved 22 October 2013.
- ^ "Obama: "Nobody is listening to your telephone calls"". CBS News. Retrieved 9 July 2013.
- ^ "Obama To Leno: 'There Is No Spying On Americans'". NPR. Retrieved 14 August 2013.
- ^ Kessler, Glenn. "James Clapper's 'least untruthful' statement to the Senate". The Washington Post. Retrieved 13 August 2013.
- ^ James Clapper interviewed by Andrea Mitchell of NBC News, June 9 2013. Retrieved 19 Sept 2013.
- ^ أ ب "DNI Clapper Letter on Misunderstandings Arising from his March 12th Appearance Before the Senate Select Committee on Intelligence". Director of National Intelligence. Archived from the original (PDF) on 16 December 2013. Retrieved 9 July 2013.
- ^ Turner, Shawn (31 July 2013). "DNI Clapper Declassifies and Releases Telephone Metadata Collection Documents". Director of Public Affairs Office of the Director of National Intelligence. Retrieved 17 August 2013.
- ^ Assistant Attorney General Roland Weich (14 December 2009). "Cover Letter and 2009 Report on the National Security Agency's Bulk Collection Program for USA PATRIOT Act Reauthorization" (PDF). U.S. Department of Justice Office of Legal Affairs. Retrieved 17 August 2013.
- ^ Assistant Attorney General Roland Weich (2 February 2011). "Cover Letters and 2011 Report on the National Security Agency's Bulk Collection Program for USA PATRIOT Act Reauthorization" (PDF). U.S. Department of Justice Office of Legal Affairs. Retrieved 17 August 2013.
- ^ Vinson, Roger (25 April 2013). "United States Foreign Intelligence Surveilllance Court Docket-Nr: BR 13–80 Primary Order for Business Records Collection Under Section 215 of the USA PATRIOT Act" (PDF). United States Foreign Intelligence Surveillance Court. Office of Director of National Intelligence. Retrieved 17 August 2013.
- ^ Paul Lewis and Spencer Ackerman (9 August 2013). "Obama touts NSA surveillance reforms to quell growing unease over program". The Guardian. Retrieved 12 August 2013.
- ^ Mark Mazzetti and Scott Shane (9 August 2013). "Threats Test Obama's Balancing Act on Surveillance". The New York Times. Retrieved 12 August 2013.
- ^ أ ب ت ث ج "Barack Obama pledges greater surveillance transparency". BBC News US & CANDA. 9 August 2013. Retrieved 12 August 2013.
- ^ "Obama pledges spy programme transparency". Al Jazeera. 10 August 2013. Retrieved 12 August 2013.
- ^ Chelsea J. Carter and Jessica Yellin (10 August 2013). "Obama: Snowden can 'make his case' in court; no Olympics boycott". CNN. Retrieved 12 August 2013.
- ^ "White House surveillance reform plan – Administration White Paper: 'Bulk Collection of Telephony Metadata under Section 215 of the USA Patriot Act'". The Washington Post. 9 August 2013. Retrieved 14 August 2013.
- ^ "Obama administration asserts broad surveillance powers". The Washington Post. 10 August 2013. Retrieved 14 August 2013.
- ^ Priest, Dana (9 August 2013). "Piercing the confusion around NSA's phone surveillance program". The Washington Post. Retrieved 14 August 2013.
- ^ أ ب Ribeiro, James (13 August 2013). "Intelligence chief Clapper to set up US surveillance review group". PC World. Retrieved 13 August 2013.
- ^ أ ب Scott Wilson and Zachary A. Goldfarb (9 August 2013). "Obama announces proposals to reform NSA surveillance". The Washington Post. Retrieved 12 August 2013.
- ^ Serwer, Adam (12 August 2013). "Intel chief misled Congress on NSA spying. Now he's leading program's review". MSNBC. Retrieved 13 August 2013.
- ^ Masnick, Mike (12 August 2013). "Confessed Liar To Congress, James Clapper, Gets To Set Up The 'Independent' Review Over NSA Surveillance". Techdirt. Retrieved 13 August 2013.
- ^ Mullin, Joe (13 August 2013). "Obama's "reform" panel to be led by Clapper, who denied spying to Congress". Ars technica. Retrieved 13 August 2013.
- ^ Peter Wallsten (11 August 2013). "Lawmakers say obstacles limited oversight of NSA's telephone surveillance program". The Washington Post. Retrieved 25 August 2013.
- ^ Johnson, Luke. "James Clapper, Director of National Intelligence Who Misled Congress, To Establish Surveillance Review Group". Huffington Post. Retrieved 13 August 2013.
- ^ Ackerman, Spencer (12 September 2013). "Obama's NSA surveillance review panel did not discuss changes, attendees say - Pair say meeting was dominated by tech firms' interests and session did not broach the topic of changes to data collectio". The Guardian. Retrieved 2 October 2013.
- ^ "US: Increase Transparency on Surveillance". Human Rights Watch. Retrieved 20 August 2013.
- ^ "UK: Detention of Guardian journalist's partner at Heathrow unlawful and unwarranted". Amnesty International. Retrieved 20 August 2013.
- ^ "Forcing The Guardian to destroy materials is a direct attack on press freedom". Index on Censorship. Retrieved 20 August 2013.
- ^ "UK: "National security concerns must never justify intimidating journalists into silence," warn UN experts". Office of the United Nations High Commissioner for Human Rights. Retrieved 4 September 2013.
- ^ Halliday, Josh. "MoD serves news outlets with D notice over surveillance leaks". The Guardian. Retrieved 27 June 2013.
- ^ "The Guardian Blocked by the Army After NSA Stories". Huffington Post. Retrieved 20 August 2013.
- ^ أ ب "The security threat posed by Snowden". The Financial Times. October 9, 2013.
- ^ "David Miranda Heathrow detention: No 10 'kept abreast of operation'". BBC News. 20 August 2013.
- ^ Boadle, Anthony (6 August 2013). "Glenn Greenwald: Snowden Gave Me 15–20,000 Classified Documents". Huffington Post. Retrieved 9 August 2013.
- ^ Greenwald, Glenn (19 August 2013). "Glenn Greenwald: detaining my partner was a failed attempt at intimidation". The Guardian. London.
- ^ "White House knew Glenn Greenwald's partner David Miranda would be detained". CNN. Retrieved 20 August 2013.
- ^ أ ب "Guardian says Britain made it destroy Snowden material". Reuters. Retrieved 20 August 2013.
- ^ David Miranda's detention had no basis in law, says former lord chancellor | World news. The Guardian. (21 August 2013).
- ^ أ ب "US given 'heads up' on David Miranda detention". BBC News. 19 August 2013.
- ^ Rusbridger, Alan (19 August 2013). "David Miranda, schedule 7 and the danger that all reporters now face". The Guardian. Retrieved 21 August 2013.
- ^ "NSA statements to The Post". The Washington Post. Retrieved 20 August 2013.
- ^ Lloyd Grove. "At the Obama White House: Transparency Transhmarency". The Daily Beast. Retrieved 23 September 2013.
- ^ أ ب "Latin American nations voice concerns to Ban over rerouting of Bolivian leader's plane". United Nations. Retrieved 20 August 2013.
- ^ Ehrenfreund, Max (25 July 2013). "House proposal to curtail NSA in response to Edward Snowden's leaks fails narrowly". The Washington Post. Retrieved 29 July 2013.
- ^ Abby Ohlheiser and Philip Bump (24 July 2013). "The Amash Amendment Fails, Barely". The Atlantic Wire. Retrieved 29 July 2013.
- ^ Kravets, David (26 July 2013). "Lawmakers Who Upheld NSA Phone Spying Received Double the Defense Industry Cash". Retrieved 3 August 2013.
- ^ Serwer, Adam (25 September 2013). "New calls for surveillance reform after Snowden". MSNBC. Retrieved 18 October 2013.
- ^ Zengerle, Patricia (25 September 2013). "U.S. lawmakers seek to end bulk NSA telephone records collection". Reuters. Retrieved 18 October 2013.
- ^ Paul Lewis and Dan Roberts (25 September 2013). "NSA reform bill to trim back US surveillance unveiled in Congress". The Guardian. Washington. Retrieved 18 October 2013.
- ^ "Brazil Reacts With Fury To NSA Spying; Mexico Orders Probe". International Business Times. Retrieved 16 September 2013.
{{cite web}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ أ ب ت "Exclusive: Brazil's Rousseff wants U.S. apology for NSA spying". Reuters. Retrieved 16 September 2013.
{{cite web}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ "China has 'mountains of data' about U.S. cyber attacks: official". Reuters. 5 June 2013. Retrieved 2013-10-24.
- ^ "China asks U.S. to explain Internet surveillance". Reuters. Retrieved 24 October 2013.
- ^ "France summons U.S. ambassador over spying report". Reuters. Retrieved 24 October 2013.
- ^ Michael Mainville. "France warns US spying claims threaten trade talks". AFP. Retrieved 24 October 2013.
- ^ "German Foreign Ministry Summons US Ambassador Over NSA Spying Claims". The Wall Street Journal'. 1 July 2013.
Seeking clarification on the matter, the foreign ministry has called the U.S. ambassador to Germany, Philip Murphy, for a meeting later Monday, a spokesman for the ministry said.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "German foreign minister summons US ambassador over Merkel spying allegations". Deutsche Welle. Retrieved 24 October 2013.
- ^ "NSA spying allegations: Are US allies really shocked?". BBC. 26 October 2013. Retrieved 26 October 2013.
- ^ "Germany ends spy pact with US and UK after Snowden". BBC. 2 August 2013.
- ^ German Helicopter Searched For NSA Listening Post In Frankfurt SPIEGEL ONLINE.
- ^ "Italy Presses Kerry Over US Surveillance". Voice of America. Retrieved 24 October 2013.
- ^ "Letta quizzes Kerry on US spy claims". Gazzetta del Sud. Retrieved 24 October 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ "Mexico foreign minister meets US envoy over spy claims". AFP. Retrieved 26 October 2013.
- ^ "Spanish PM summons U. S. ambassador over NSA spying". Agenzia Giornalistica Italia. Retrieved 27 October 2013.
- ^ "NSA surveillance: Spain demands US explain 'monitoring'". bbc.co.uk. 28 October 2013. Retrieved 28 October 2013.
- ^ "European Union threatens to stop sharing data with United States over spying reports". Daily News. Retrieved 8 July 2013.
- ^ "Rules Shielding Online Data From N.S.A. and Other Prying Eyes Advance in Europe", James Kanter and Mike Scott, New York Times, 21 October 2013. Retrieved 22 October 2013.
- ^ "EU-US spying row stokes concern over anti-terror campaign". EU Business. 26 October 2013. Retrieved 26 October 2013.
- ^ "EU says distrust of US on spying may harm terror fight". BBC. 25 October 2013. Retrieved 26 October 2013.
- ^ Roulo, Claudette. "Leaks Damage National Security, NSA Director Says". American Forces Press Service. Archived from the original on 16 December 2013. Retrieved 8 July 2013. (Archive)
- ^ Corera, Gordon (October 4, 2013). "Edward Snowden revelations: Can we trust the spying state?". BBC.
- ^ Edward Snowden: Russia, China Did Not Get Any Documents From Me
- ^ Whitehead, Tom (October 9, 2013). "GCHQ leaks have 'gifted' terrorists ability to attack 'at will', warns spy chief". Daily Telegraph.
- ^ أ ب Gardner, Timothy; Hosenball, Mark (June 9, 2013). "Spy agency seeks criminal probe into leaks". Reuters. Retrieved June 9, 2013.
- ^ Blake, Aaron (June 9, 2013). "Clapper: Leaks are 'literally gut-wrenching,' leaker being sought". The Washington Post. Retrieved August 8, 2013.
- ^ Finn, Peter; Horwitz, Sari (June 21, 2013). "U.S. charges Snowden with espionage". The Washington Post. Retrieved June 21, 2013.
- ^ U.S. vs. Edward J. Snowden criminal complaint. The Washington Post.
- ^ أ ب Ackerman, Spencer; Roberts, Dan (June 28, 2013). "US army blocks access to Guardian website to preserve 'network hygiene'". The Guardian. London. Retrieved June 29, 2013.
- ^ Ackerman, Spencer (July 1, 2013). "US military blocks entire Guardian website for troops stationed abroad". The Guardian.
- ^ Raddatz, Martha (August 4, 2013). "Transcript for Joint Chiefs Chairman Gen. Martin Dempsey on 'This Week'". ABC News 'This Week'. Retrieved August 14, 2013.
- ^ "Obama downplays Snowden case, says US not 'scrambling jets' to get 'hacker'". Fox News. June 27, 2013.
- ^ Pecquet, Julian (June 27, 2013). "US won't 'scramble jets' to capture 'hacker' Snowden, Obama says". The Hill.
- ^ أ ب Wolf, Z. Byron (August 13, 2013). "Fact-checking Obama's claims about Snowden". CNN.
- ^ MacAskill, Ewen (August 13, 2013). "White House insists James Clapper will not lead NSA surveillance review". The Guardian.
- ^ Farivar, Cyrus (August 23, 2013). "Obama's 'outside experts' surveillance review panel has deep ties to gov't". Ars Technica.
- ^ Waterman, Shaun (12 September 2013). "Congress will rein in NSA's domestic snooping, predicts top U.S. intel official". The Washington Times. Retrieved 16 September 2013.
- ^ Dilanian, Ken (12 September 2013). "Clapper: Snowden case brings healthy debate; more disclosures to come". The Los Angeles Times. Retrieved 15 September 2013.
- ^ Reeve, Elspeth (June 10, 2013). "Washington turns on the NSA blinders to target weird 'IT guy' leaker instead". The Atlantic Wire.
- ^ LoGiurato, Brett (June 11, 2013). "John Boehner: Edward Snowden Is A 'Traitor'". San Francisco Chronicle. Retrieved June 11, 2013.
- ^ أ ب Herb, Jeremy; Sink, Justin (June 10, 2013). "Sen. Feinstein calls Snowden's NSA leaks an 'act of treason'". thehill.com.
- ^ Nelson, Bill (June 11, 2013). "This man is a traitor". Daily News. New York.
- ^ "Edward Snowden: Ex-CIA leaker drops out of sight, faces legal battle". The Chicago Tribune. Reuters. June 10, 2013. Retrieved June 12, 2013.
- ^ Blake, Aaron (June 11, 2013). "DNC chair Debbie Wasserman Schultz: Snowden is a coward". The Washington Post. Retrieved June 13, 2013.
- ^ Dumain, Emma; Lesniewski, Niels (June 10, 2013). "Snowden Has a Few Defenders on the Hill". Roll Call. Retrieved June 11, 2013.
- ^ Morgenstern, Madeleine (June 11, 2013). "Ted Cruz Reserving Judgement on Whether NSA Leaker Is a 'Patriot' or a 'Traitor'". The Blaze. Retrieved June 11, 2013.
- ^ Sink, Justin (June 11, 2013). "Rand Paul 'reserving judgment' on NSA leaker". The Hill.
- ^ Sullivan, Sean (June 23, 2013). "Rand Paul: Snowden will face problems if he 'cozies up' to Russia, China". The Washington Post.
- ^ "Rand Paul: Edward Snowden 'civil disobedient' – Tal Kopan –". Politico.com. June 18, 2013.
- ^ "John Lewis compares Edward Snowden, Gandhi – James Arkin –". Politico.com. August 8, 2013.
- ^ "This man is a traitor". senate.gov. Retrieved 18 September 2013.
- ^ "John Boehner: Edward Snowden Is A 'Traitor'". The Huffington Post. Retrieved 18 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ S. 1372 at THOMAS. S. 1372 at GovTrack. S. 1372 at OpenCongress.
- ^ Zengerle, Patricia (July 25, 2013). "U.S. lawmakers want sanctions on any country taking in Snowden". Reuters.
- ^ "U.S. Senate advances law pressuring Russia not to give Snowden asylum". Xinhua. July 26, 2013.
- ^ "FY14 Full Committee Markup of State-Foreign Operations, and Financial Services General Government Bills" (Podcast). United States Senate Committee on Appropriations. July 25, 2013. Event occurs at 1:10:08.
- ^ Max Ehrenfreund. "House proposal to curtail NSA in response to Edward Snowden's leaks fails narrowly". The Washington Post.
- ^ "The Amash Amendment Fails, Barely – Abby Ohlheiser and Philip Bump". The Atlantic Wire. July 24, 2013.
- ^ "Amash: Snowden a whistle-blower, 'told us what we need to know'". Fox News. 4 August 2013. Retrieved 6 October 2013.
- ^ Raddatz, Martha (August 4, 2013). "'This Week' Transcript: Gen. Martin Dempsey, Reps. Ruppersberger and King, and Glenn Greenwald". ABC News 'This Week'. Retrieved August 14, 2013.
- ^ "McCain: Young Americans admire Snowden, see him as 'some kind of Jason Bourne'". The Washington Times. Retrieved August 11, 2013.
- ^ Johnson, Luke. "Edward Snowden Receives Support From Former GOP Sen. Gordon Humphrey". Huffington Post. Retrieved August 11, 2013.
- ^ Greenwald, Glenn. "Email exchange between Edward Snowden and former GOP Senator Gordon Humphrey". The Guardian. Retrieved August 11, 2013.
- ^ Gold, Hadas. "Former Sen. Gordon Humphrey emails with Edward Snowden". Politico. Retrieved July 17, 2013.
- ^ "Rep. McClintock Says the US Should Grant Snowden Amnesty – Hit & Run". Reason. July 24, 2013.
- ^ Newport, Frank (June 12, 2013). "Americans Disapprove of Government Surveillance Programs". Gallup.
- ^ "Public Split over Impact of NSA Leak, But Most Want Snowden Prosecuted". Pew Research Center. June 17, 2013.
{{cite journal}}: Cite journal requires|journal=(help) - ^ Page, Susan (June 18, 2013). "Poll: Snowden should be prosecuted for NSA leaks". USA Today. Washington DC.
- ^ "Post-ABC poll: NSA surveillance and Edward Snowden". The Washington Post. June 19, 2013.
- ^ Emily Swanson (July 5, 2013). "Edward Snowden Poll Finds More Americans Now Think He Did The Wrong Thing". Huffington Post. Retrieved July 9, 2013.
See more polls reported in early July, see here [1].
- ^ Rebecca Ballhaus (July 24, 2013) WSJ/NBC Poll: Most Americans View Snowden Negatively The Wall Street Journal
- ^ أ ب Salant, Jonathan D. (July 10, 2013). "Snowden Seen as Whistle-Blower by Majority in New Poll". Bloomberg News. Retrieved July 10, 2013.
- ^ Nelson, Steven (August 1, 2013). "As Edward Snowden receives asylum in Russia, poll shows Americans sympathetic to NSA 'whistle-blower'". US News & World Report.
- ^ Heather, Kelly. "Protests against the NSA spring up across U.S." CNN. Retrieved 13 August 2013.
- ^ "Thousands fill German streets to protest Berlin's NSA spying involvement". Russia: RT. Retrieved 13 August 2013.
- ^ Bart Jansen and Carolyn Pesce. "Anti-NSA rally attracts thousands to march in Washington". USA Today. Retrieved 27 October 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Thousands gather in Washington for anti-NSA 'Stop Watching Us' rally | World news | theguardian.com
- ^ Greenwald, Glenn (June 22, 2013). "On the Espionage Act charges against Edward Snowden". The Guardian Security and Liberty blog. London. Archived from the original on June 23, 2013. Retrieved June 23, 2013.
{{cite news}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ Guariglia, Matthew (June 10, 2013). "Edward Snowden: Traitor or Hero?". heavy.com. Retrieved June 11, 2013.
- ^ Cassidy, John (June 10, 2013). "Why Edward Snowden Is A Hero". The New Yorker.
- ^ Rushkoff, Douglas (June 10, 2013). "Edward Snowden is a hero". CNN. Retrieved June 16, 2013.
- ^ Davidson, Amy (June 9, 2013). "Edward Snowden, The N.S.A. Leaker, Comes Forward". The New Yorker.
- ^ Harvey, Fiona (June 19, 2013). "NSA surveillance is an attack on American citizens, says Noam Chomsky". The Guardian. London. Retrieved July 4, 2013.
- ^ "New Yorkers Declare 'I Stand With Edward Snowden': Dozens Rally & Draw Massive Media Attention for NSA Whistleblower (updated)". the sparrow project. June 10, 2013. Retrieved June 11, 2013.
- ^ أ ب Gold, Hadas (June 10, 2013). "Glenn Beck, Michael Moore call Edward Snowden a hero". Politico. Retrieved June 11, 2013.
- ^ "Cornel West Calls Edward Snowden the 'John Brown' of National Security". colorlines. June 28, 2013. Retrieved July 4, 2013.
- ^ Budowsky, Brent (June 7, 2013). "Matt Drudge, Bernie Sanders and Ron Paul versus Barack Obama, George W. Bush and Big Brother". The Hill. Washington DC. Retrieved June 11, 2013.
- ^ "Arrest Congressman Peter King, Not NSA Whistleblower". Infowars. June 10, 2013. Retrieved June 11, 2013.
- ^ "Napolitano: NSA Leaker Is an "American Hero"". Fox News Channel. June 10, 2013. Retrieved July 4, 2013.
- ^ "Oliver Stone calls National Security Agency secret-leaker Edward Snowden 'a hero'". July 4, 2013.
- ^ Kirell, Andrew (June 11, 2013). "Michael Savage Rants Against Fox News' 'Empty Skirts' & 'Lipstick With Legs' For Condemning NSA Leaker". Mediaite. Retrieved June 12, 2013.
- ^ Walt, Stephen (July 8, 2013). "Snowden deserves an immediate presidential pardon". Financial Times. Retrieved July 8, 2013.
- ^ Reeve, Elspeth (June 10, 2013). "These Pundits Have Decided Snowden Deserves to Go to Jail". The Atlantic Wire. Washington DC. Retrieved June 12, 2013.
- ^ أ ب Toobin, Jeffrey (June 10, 2013). "Edward Snowden is no hero". The New Yorker.
- ^ "Edward Snowden is a 'traitor' and possible spy for China – Dick Cheney". The Guardian. Retrieved 18 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Branigin, William (July 17, 2013). "Lawmakers of both parties voice doubts about NSA surveillance programs". The Washington Post.
- ^ Former CIA, NSA chief Michael Hayden: Open spy programs to reassure U.S. public, The Washington Times, June 30, 2013. Retrieved Jul 9, 2013.
- ^ Former CIA, NSA director sounds off on PRISM, spying tools, Network World, July 1, 2013. Retrieved Jul 9, 2013.
- ^ Peterson, Andrea. "Former NSA chief: 'Morally arrogant' Snowden will probably become an alcoholic". The Washington Post. Retrieved 18 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Schindler, John R. (June 27, 2013). "Snowden in the U.S.-Russian 'SpyWar'". National Affairs.
- ^ Ross, Brian (June 26, 2013). "Edward Snowden Steps Into Secret U.S.-Russia Spy Scuffle". ABC News
- ^ Ewing, Philip (June 25, 2013). "What Russian intel might ask Edward Snowden". Politico.
- ^ Simon Schuster (July 10, 2013). Snowden in Moscow: What Russian Authorities Might Be Doing With the NSA Whistle-Blower Time
- ^ Snowden: I never gave any information to Chinese or Russian governments, Glenn Greenwald, July 10, 2013
- ^ Watkins, Tom (June 30, 2013). "Father proposes deal for Snowden's voluntary return", CNN
- ^ The Editors (June 24, 2013). "This Is Not About Edward Snowden". Bloomberg News. New York. Retrieved June 25, 2013.
{{cite news}}:|author=has generic name (help) - ^ Greenwald, Glenn (July 3, 2013). "James Clapper, EU play-acting, and political priorities". The Guardian Security and Liberty blog (London). Retrieved July 3, 2013.
- ^ Berenson, Alex (June 25, 2013). "Snowden, Through the Eyes of a Spy Novelist". The New York Times. Retrieved June 26, 2013.
- ^ "NSA leaker petition hits 100,000-signature threshold in under 2 weeks". RT USA. June 18, 2013. Retrieved June 25, 2013.
- ^ White House Remains Silent on 'Pardon Edward Snowden' Petition - Washington Whispers (usnews.com)
- ^ Three Months After It Cleared The 100K Signature Threshold, 'Pardon Snowden' Petition Still Unanswered | Techdirt
- ^ أ ب ت ث Poulsen, Kevin (August 8, 2013). "Edward Snowden's email provider shuts down amid secret court battle". Wired.
- ^ Associated Press (August 8, 2013). "Texas-based secure email service linked to NSA leaker Edward Snowden abruptly shuts down". The Washington Post.
- ^ Masnick, Mike (August 8, 2013). "Edward Snowden's email provider, Lavabit, shuts down to fight gov't intrusion". Techdirt.
- ^ Hill, Kashmir (August 8, 2013). "Email company reportedly used by Edward Snowden shuts down rather than hand over data to the Feds". Forbes.
- ^ Schneier, Bruce (August 22, 2013). "The real, terrifying reason why British authorities detained David Miranda". The Atlantic.
- ^ "Lavabit privacy row: second email service closes 'to prevent spying' | Technology". The Guardian.
- ^ Glenn Greenwald (August 9, 2013). "Email service used by Snowden shuts itself down, warns against using US-based companies". The Guardian.
- ^ "Data snooping: law abiding citizens have 'nothing to fear', says Hague – video". The Guardian (London). June 9, 2013.
- ^ "NSA Prism programme: William Hague makes statement on GCHQ – video". The Guardian (London). June 10, 2013.
- ^ Travis, Alan; Connolly, Kate; Watt, Nicholas (June 26, 2013). "GCHQ surveillance: Germany blasts UK over mass monitoring". The Guardian. London.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ Staines, Paul (June 8, 2013). "D-Notice, June 7, 2013". Guido Fawkes blog.
- ^ 'Key Partners': The Secret Link Between Germany and the NSA July 22, 2013 Spiegel Online
- ^ "2013 Sakharov Prize for Freedom of Thought - seven nominations". 2013-09-16. Retrieved 2013-09-18.
Edward Snowden - nominated by the Greens/EFA group and GUE/NGL group
- ^ "Pakistan's Malala, Snowden Nominated for E.U. Prize". 2013-09-16. Retrieved 2013-09-18.
- ^ Valentina Pop (July 8, 2013). "Germany defends intelligence co-operation with US". EUobserver. Retrieved July 9, 2013.
- ^ Trittin, Jürgen (July 2, 2013). "Edward Snowden deserves shelter in Germany". The Guardian. United Kingdom. Retrieved July 13, 2013.
- ^ أ ب "UN rights chief urges protection for individuals revealing human rights violations". United Nations. Retrieved August 4, 2013.
- ^ Amnesty International meets US whistleblower Edward Snowden July 12, 2013
- ^ "USA must not hunt down whistleblower Edward Snowden". Amnesty International. Retrieved June 25, 2013.
- ^ USA must not persecute whistleblower Edward Snowden July 2, 2013 Amnesty
- ^ "US: Protect National Security Whistleblowers". Human Rights Watch. Retrieved June 25, 2013.
- ^ Countries Should Consider Snowden’s Asylum Claim Fairly". Human Rights Watch, July 2013
- ^ "US needs to protect whistleblowers and journalists". Index on Censorship. Retrieved August 4, 2013.
- ^ Heise Online-Autoren Detlef Borchers, anw (July 23, 2013). "Whistleblower-Preis für Edward Snowden". Heise Online. Archived from the original on July 25, 2013. Retrieved July 25, 2013.
- ^ Sven Lüders (July 24, 2013). "Fritz-Bauer-Preis an Edward Snowden". Humanistischer Pressedienst. Archived from the original on July 25, 2013. Retrieved July 25, 2013.
- ^ But, Joshua (June 16, 2013). "Hongkongers don't want Snowden handed over to the US, according to poll". South China Morning Post. Hong Kong. Retrieved June 17, 2013.
- ^ "HK, US govt lawyers 'not working together' on Snowden, say sources as CY breaks silence". South China Morning Post. Hong Kong. June 16, 2013.
- ^ Fraser, Niall (June 13, 2013). "H.K. lawmakers petition Obama for leniency against whistleblower". Kyodo News International. Retrieved June 15, 2013.
- ^ Ma, Mary (June 20, 2013). "Ip in security minister's shoes". The Standard. Hong Kong.
However, surrounding the Snowden case is something never before seen in local politics. Not only are the pan-democrat and pro-establishment camps singing off the same song sheet, the pan-democrats and mainland propagandists are humming a similar tune.
- ^ Lau, Stuart (June 24, 2013). "Hong Kong's political foes made allies amid Edward Snowden storm". South China Morning Post. Hong Kong. Retrieved June 24, 2013.
Snowden's arrival in the city gave Hong Kong a rare place in the global geopolitical spotlight and ushered in near-unprecedented political solidarity as pan-democrats and Beijing loyalists lined up to take a shot at an unlikely target: the United States.
- ^ أ ب Zuo, Mandy (June 20, 2013). "Beijing wants Hong Kong to handle Snowden on its own, party newspapers suggest". South China Morning Post. Hong Kong. Retrieved June 20, 2013. In print as "Articles highlight possible Beijing role".
{{cite news}}: CS1 maint: postscript (link) - ^ Lai Ying-kit (June 24, 2013). "Edward Snowden's depature seen as a relief: Chinese-language newspapers". South China Morning Post. Hong Kong. Retrieved June 24, 2013.
- ^ "Beijing made final decision, say analysts". South China Morning Post. Hong Kong. June 25, 2013. p. 2.
- ^ Kaiman, Jonathan (June 25, 2013). "China's state newspaper praises Edward Snowden for 'tearing off Washington's sanctimonious mask'". The Guardian. London. Retrieved June 25, 2013.
- ^ "Ecuador warned: Asylum for Edward Snowden would jeopardize millions in trade". Michelle Malkin. June 27, 2013.
- ^ "Ecuador offers U.S. rights aid, waives trade benefits". Reuters. June 27, 2013.
- ^ "Ecuador waives US trade rights after threats made over Snowden case". South China Morning Post. Hong Kong. June 28, 2013.
- ^ "Ecuador president blasts coverage of Snowden case". Newsday. New York. Associated Press. June 26, 2013. Archived from the original on June 29, 2013. Retrieved June 28, 2013.
- ^ Snowden's fate up in the air after Nicaragua, Venezuela offer asylum, CTV Television Network, July 5, 2013. Retrieved July 9, 2013.
- ^ Sotero, Paulo (17 September 2013). "Mission impossible in Moscow". O Estado de S. Paulo. Retrieved 18 September 2013.
- ^ Leahy, Joe (18 September 2013). "Brazil's Petrobras to invest heavily in data security". Financial Times. São Paulo. Retrieved 18 September 2013. قالب:Registration
- ^ أ ب Pilkington, Ed. "Edward Snowden's digital 'misuse' has created problems, says Ban Ki-moon." The Guardian. July 3, 2013. Retrieved July 3, 2013.
- ^ G20 summits: Russia and Turkey react with fury to spying revelations, The Guardian, June 17, 2013. Retrieved Jul 2013.
- ^ O'Malley, Nick (June 10, 2013). "NSA leaker reveals himself after fleeing US". The Sydney Morning Herald. Retrieved June 10, 2013.
- ^ Ellsberg, Daniel (June 10, 2013). "Edward Snowden: saving us from the United Stasi of America". The Guardian. Retrieved June 10, 2013.
- ^ Noor, Jaisal (June 11, 2013). "Former CIA Analyst: Snowden Did The Right Thing". The Real News Network.
- ^ أ ب Eisler, Peter; Page, Susan (June 16, 2013). "3 NSA veterans speak out on whistle-blower: We told you so." USA Today (Washington DC). Retrieved June 19, 2013.
- ^ Snowden saw what I saw: surveillance criminally subverting the constitution The Guardian. Retrieved July 10, 2013
- ^ Addley, Esther (June 10, 2013). "Julian Assange praises Edward Snowden as a hero". The Guardian. London. Retrieved June 10, 2013.
- ^ Dart, Tom (June 22, 2013). "Support NSA whistleblower Edward Snowden, says Julian Assange". The Guardian (London). Retrieved June 22, 2013.
- ^ David Jackson. "Assange: Obama 'validates' Snowden". USA Today.
- ^ "Assange calls Obama reform plans 'victory of sorts' for Snowden". Reuters. August 10, 2013.
- ^ Blowback from the White House's vindictive war on whistleblowers." Leibowitz, Shamai in The Guardian. July 5, 2013. Retrieved July 5, 2013.
- ^ The Washington Post
- ^ Former National Security Whistleblowers Meet in Moscow and Award Sam Adams Prize to Snowden - Government Accountability Project
- ^ 'US unchained itself from constitution': Whistleblowers on RT after secret Snowden meeting — RT News
- ^ John Hudson. "Exclusive: After Multiple Denials, CIA Admits to Snooping on Noam Chomsky". Foreign Policy. Retrieved 27 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Nikhil Kumar. "Memo shows CIA 'did keep file on Noam Chomsky'". The Independent. Retrieved 27 September 2013.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help) - ^ أ ب ت ث ج ح خ MATTHEW M. AID. "Secret Cold War Documents Reveal NSA Spied on Senators". Foreign Policy. Retrieved 25 September 2013.
...That's according to a recently declassified NSA history, which called the effort "disreputable if not outright illegal." For years the names of the surveillance targets were kept secret. But after a decision by the Interagency Security Classification Appeals Panel, in response to an appeal by the National Security Archive at George Washington University, the NSA has declassified them for the first time. The names of the NSA's targets are eye-popping.
{{cite web}}: Italic or bold markup not allowed in:|publisher=(help)
قراءات إضافية
- "The NSA Files". The Guardian.
- Politico Staff. "NSA leaks cause flood of political problems." Politico. 13 June 2013.
- NSA inspector general report on email and internet data collection under Stellar Wind as provided by The Guardian on 27 June 2013.
- "Putin talks NSA, Syria, Iran, drones in exclusive RT interview (FULL VIDEO)." Russia Today. 12 June 2013.
- Ackerman, Spencer. "NSA warned to rein in surveillance as agency reveals even greater scope." The Guardian. 17 July 2013.
- Ackerman, Spencer. "Slew of court challenges threaten NSA's relationship with tech firms." The Guardian. Wednesday 17 July 2013.
- Ackerman, Spencer and Paul Lewis. "NSA amendment's narrow defeat spurs privacy advocates for surveillance fight." The Guardian. Thursday 25 July 2013.
- Ackerman, Spencer and Dan Roberts. "US embassy closures used to bolster case for NSA surveillance programs." The Guardian. Monday 5 August 2013.
- Greenwald, Glenn. "Members of Congress denied access to basic information about NSA." The Guardian. Sunday 4 August 2013.
- "Obama’s former adviser ridicules statement that NSA doesn’t spy on Americans." (Archive) Russia Today. 9 August 2013.
- MacAskill, Ewen. "Justice Department fails in bid to delay landmark case on NSA collection." The Guardian. Thursday 25 July 2013.
- Rushe, Dominic. "Microsoft pushes Eric Holder to lift block on public information sharing." The Guardian. Tuesday 16 July 2013.
- Perez, Evan. "Documents shed light on U.S. surveillance programs." (Archive) CNN. 9 August 2013.
- Gellman, Barton. "NSA broke privacy rules thousands of times per year, audit finds." Washington Post. Thursday 15 August 2013.
- Roberts, Dan and Robert Booth. "NSA defenders: embassy closures followed pre-9/11 levels of 'chatter'." The Guardian. Sunday 4 August 2013.
- Greenwald, Glenn. "The crux of the NSA story in one phrase: 'collect it all'." The Guardian. Monday 15 July 2013.
- Sanchez, Julian. "Five things Snowden leaks revealed about NSA’s original warrantless wiretaps." Ars Technica. 9 July 2013.
- Forero, Juan. "Paper reveals NSA ops in Latin America." Washington Post. 9 July 2013.
- Jabour, Bridie. "Telstra signed deal that would have allowed US spying." The Guardian. Friday 12 July 2013.
- Ackerman, Spencer. "White House stays silent on renewal of NSA data collection order." The Guardian. Thursday 18 July 2013.
- Naughton, John. "Edward Snowden's not the story. The fate of the internet is." The Guardian. 28 July 2013.
- Adams, Becket. "MAD MAGAZINE USES ICONIC CHARACTERS TO HIT OBAMA OVER GOV’T SURVEILLANCE." The Blaze. 8 August 2013.
- Howerton, Jason. "HERE IS THE PRO-NSA SURVEILLANCE ARGUMENT." The Blaze. 10 June 2013.
- "Edward Snowden NSA files: secret surveillance and our revelations so far – Leaked National Security Agency documents have led to several hundred Guardian stories on electronic privacy and the state" by the Guardian's James Ball on 21 August 2013
- 2013-07-29 Letter of FISA Court president Reggie B. Walton to the Chairman of the U.S. Senate Judiciary Committee Patrick J. Leahy about certain operations of the FISA Court; among other things the process of accepting, modifying and/or rejecting surveillance measures proposed by the U.S. government, the interaction between the FISA Court and the U.S. government, the appearance of non-governmental parties before the court and and the process used by the Court to consider and resolve any instances where the government entities notifies the court of compliance concerns with any of the FISA authorities.
- "The Spy Files". Wikileaks. December 1, 2011. A collection of documents relating to surveillance.
- "The Spy Files". Wikileaks. December 8, 2011. Part 2 of the above.
- "Spy Files 3". Wikileaks. September 4, 2013. Part 3 of the above.
- "Veja os documentos ultrassecretos que comprovam espionagem a Dilma" (in Portuguese). 2 September 2013. Retrieved 4 September 2013.
{{cite web}}: CS1 maint: unrecognized language (link) Documents relating to the surveillance against Dilma Roussef and Enrique Peña Nieto - NSA surveillance: A guide to staying secure - The NSA has huge capabilities – and if it wants in to your computer, it's in. With that in mind, here are five ways to stay safe by The Guardian's Bruce Schneier on September 5, 2013.
- CS1 errors: markup
- CS1 errors: unsupported parameter
- CS1 errors: deprecated parameters
- CS1 errors: generic name
- CS1 maint: postscript
- Articles with hatnote templates targeting a nonexistent page
- Pages using quote template with unknown parameters
- Pages with timeline metadata
- Pages using div col with unknown parameters
- Pages with empty portal template
- عمليات وكالة الأمن القومي
- تجسس جماعي
- جدل في 2013
- إدوارد سنودن
- التنصت على كابلات الاتصالات البحرية